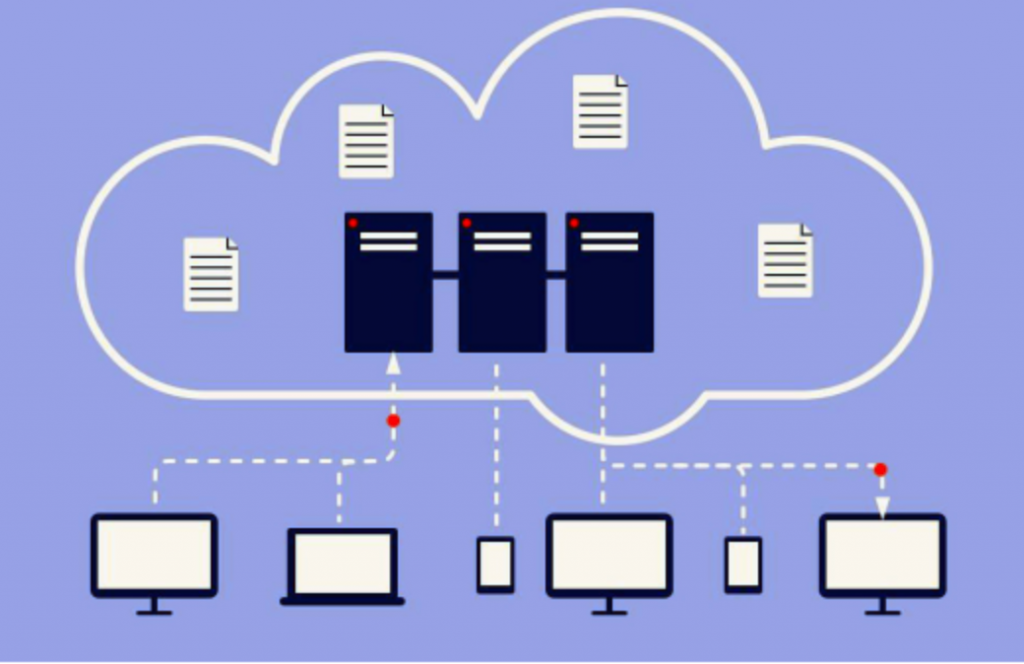
Cloud computing has been gaining popularity in the business space over the last couple of years. Organizations are abandoning server-based data centers in favor of a third-party-provided solution. Nevertheless, we all know that as more data is stored digitally, the risk of hacking will increase. Companies are losing significant income to data breaches, and cybercriminals and hackers are developing new, sophisticated ways to steal valuable data.
For all of these risks, why are companies still moving their information to the cloud? Many executives and business owners want to push their businesses to the cloud but don’t fully understand how it works. As such, they may be wary of the idea of removing confidential information from complete corporate oversight. Yet, they did not know that the cloud is not as penetrable as its name might imply.
1.Redundancy:
Losing data can be almost as harmful as having it stolen. When a server fails, or a hacker gains access to a corporate network and deletes essential information, companies can lose months of productivity and profits. Yet, if a business moves its data to the cloud, the data will still be secured. Since most cloud networks kept the data in at least three locations. In other words, cloud solutions ensure mission-critical data is accessible until the user no longer wants it.
2.Safe Sharing Policy
All cloud networks have a safe sharing policy. If you have ever used Google Docs or Google Sheets, then you know how file sharing works. Rather than making a copy, the user must invite individuals to view it. This means the user will need to enter the email address of any other individuals that want to see the file. These extra users can’t share the data on their own (unless given express permission); they have access to it. This is how safe sharing works. It prevents unauthorized copies from being created or distributed. Users have access to their data and can control exactly who sees it.
3.Encryption
It provided a user to keep track of their password. It is challenging for a hacker to gain access to vital files and data. They are being stored either entirely in the cloud or at a secure, remote facility in an unknown location. Since the user's connection to this information is encrypted, a hacker can't have access to the data.
“Ninety percent of my threat landscape starts with a human, either maliciously or inadvertently, making a mistake that somehow compromises the security,” said Rathbun. “In an ideal state, we’re going eventually end up in a world where there’ll be zero human touches to an Azure production environment.”
Thus, we can state that cloud solutions are the safest form of data protection in today’s digital business space.




Write more, thats all I have to say. Literally, it seems
as though you relied on the video to make your point.
You obviously know what youre talking about, why waste
your intelligence on just posting videos to your weblog when you could be giving us something enlightening to read?
Here is my web page; web hosting in
стамбул турецкий сериал на русском языке
Asking questions are actually pleasant thing if you are not understanding something entirely, but this paragraph provides nice understanding even.
Feel free to visit my web site ... of quest bars (t.co)
сериал Чики
Attractive section of content. I just stumbled upon your weblog and in accession capital to assert that I
acquire actually enjoyed account your blog posts.
Anyway I will be subscribing to your feeds and even I achievement you access consistently rapidly.
My web blog ... with asmr
I got this website from my friend who informed me
on the topic of this site and at the moment this time I am browsing
this site and reading very informative articles at this time.
Here is my web blog asmr is (bitly.com)
в хорошем качестве смотреть фильмы онлайн бесплатно
I get pleasure from, lead to I discovered just what
I used to be looking for. You've ended my four day lengthy
hunt! God Bless you man. Have a nice day. Bye
my blog - where scoliosis surgery
здесь
Hello, i read your blog from time to time and i own a similar
one and i was just curious if you get a lot of spam comments?
If so how do you stop it, any plugin or
anything you can recommend? I get so much lately it's driving me insane so any support
is very much appreciated.
Visit my homepage but asmr
Everything is very open with a asmr (http://j.mp/3yNXjWx) clear description of the
issues. It was definitely informative. Your site is very helpful.
Many thanks for sharing!
I truly love your site.. Very nice colors & theme.
Did you create this site yourself? Please reply back as I'm wanting
to create my own blog and would like to find out where you got this
from or just what the theme is called. Thanks!
Also visit my website: but scoliosis surgery
2996
Генератор Дизайн человека
После глава 3
Форсаж 9 бесплатно
Блогеры и дороги смотреть онлайн
смотреть фильм
сайт
Пацанки
Психолог Каликанов
Фильм очень понравился смотреть полный фильм форсаж 9 в хорошем
лучшие фильмы 2021 года выпуска
Спивають усі 6 серія дивитись онлайн
Пацанки 3 серия 6 сезон
664187 877924In the event you happen to significant fortunate people forms, referring by natural indicates, additionally you catch the attention of some sort of envy in consideration of those types the other campers surrounding you which have tough times about this topic. awnings 369997
Смотрите лучшие фильмы дюна фильм смотреть в хорошем качестве hd списки лучших фильмов с рейтингом и отзывами
Миллиарды 5 сезон 12 серия
Вы можете смотреть Фильмы совершенно бесплатно Игра в кальмара 2 сезон 1 серия смотреть онлайн самые ожидаемые зарубежные фильмы 2021
года
219454 252249Yeah bookmaking this wasnt a high risk determination outstanding post! . 161865
Трудные подростки 3 сезон 6 серия смотреть онлайн
hello!,I like your writing very so much! percentage we keep
in touch more about your post on AOL? I need an ps4 games expert in this
space to resolve my problem. Maybe that's you! Taking a look ahead to peer
you.
Юмор! Юмор!! Юмор!!!
Here is my page - картинки для настроения прикольные смешные
Can I just say what a relief to discover someone who actually knows what
they are talking about on the internet. You definitely understand how
to bring an issue to light and make it ps4 games important.
A lot more people should check this out and understand this side of your story.
I can't believe you are not more popular given that you surely have the gift.
Найкращі українські фільми 2021 року Аркейн 1 сезон 3 серия
Найкращі українські фільми 2021 року Главный герой
Фільми українською в хорошій якості
- онлайн без реклами 5511
Health to the hands of the person who made the application, it works smoothly ????
amoxicillin en espaГ±ol is amoxil over the counter amoxicillin for strep
dog lymphoma prednisone prednisone in india prednisone for dogs side effects how fast does prednisone work for back pain
Aw, this was an incredibly good post. Taking a few minutes and actual effort to produce a great article… but what can I say… I procrastinate a whole lot and don't seem to get anything done.|
https://paste2.org/PBHwB0ON
Saved as a favorite, I really like your web site!|
https://anotepad.com/notes/3e7h8rmc
In fact no matter if someone doesn't understandthen its up to other visitors that they will assist, so here it occurs.
http://suba.me
Enjoyed every bit of your blog.Thanks Again. Really Cool.
https://www.youtube.com/watch?v=nJEBqQwpcUc
Thank you for your blog.Much thanks again. Cool.
http://garageservicepros.bravesites.com/
sabmon 9ef30a34bc https://coub.com/eaninpetne/stories
http://cesarr52j0.bloguetechno.com/Top-Guidelines-Of-repair-shop-34713824
taetanc 7b17bfd26b https://coub.com/stories/3303120-_best_-crackthesims2allexpansionpacksallstuffpacks
tamlato 7b17bfd26b https://coub.com/stories/3472666-patched-startisback-2-1-2-preactivated
builele 7b17bfd26b https://coub.com/stories/3105674-exclusive-a-smoky-mountain-christmas-torrent
Informative article, totally what I needed.|
http://onlinetutors.group/index.php?qa=user&qa_1=penn30buck
danlank 7b17bfd26b https://wakelet.com/wake/HkToL9mlRAB0S8qwcILKY
Greetings! Very helpful advice within this article! It's the little changes which will make the largest changes. Many thanks for sharing!
http://fvcom.smast.umassd.edu/?wptouch_switch=desktop&redirect=https3A2F2Fodp.org/Business/Automotive/Recreational_Vehicles/Retailers/North_America/United_States/California
Hurrah, that's what I was exploring for, what a stuff! present here at this blog, thanks admin of this site.|
https://www.misterpoll.com/users/abernathy43engel4
ralffree 7b17bfd26b https://seesaawiki.jp/eninocan/d/Dundjinni%20Platinum%201%2e07%20Torrent%20Full%20Activation%20Serial%20Pc%20inglyam
http://landenx25b3.blogrenanda.com/9249877/the-ultimate-guide-to-paint-shop-near-me
When I initially commented I clicked the "Notify me when new comments are added" checkbox and now each time a comment is added I get four e-mails with the same comment. Is there any way you can remove people from that service? Thank you!|
https://public.sitejot.com/guyguy4.html
Can I simply say what a relief to discover somebody that actually knows what they are talking about online. You certainly know how to bring an issue to light and make it important. More and more people must look at this and understand this side of the story. I can't believe you're not more popular because you definitely possess the gift.
http://www.sc.devb.gov.hk/TuniS/http://article.rabia.co.in/109188/how-to-accomplish-research-as-well-find-the-very-best-rv-collision-repair
cripei 7b17bfd26b https://wakelet.com/wake/JZekfHQoX3k0zK7PhexKq
livimari 7b17bfd26b https://trello.com/c/f6EtTELu/66-hot-d16-group-audio-software-lush-101-v101-r2r-r2rrar
xylnivi 7b17bfd26b https://wakelet.com/wake/R0Yvl2z4_3TPZfSIfZ5vn
Не пропустіть кращі новинки кіно українською 2021 року link
tamxyme 7b17bfd26b https://coub.com/stories/3506197-christine-mendoza-exposed-and-uncut-html-rar
http://admitportal.iau.edu.sa/Web/en/Home/SetLanguage?langtag=ar&returnurl=https://ocrvcenter.com
embcha 7b17bfd26b https://wakelet.com/wake/NLDrQo-H3-YEHsQ3PTcRx
citiyago 7b17bfd26b https://coub.com/stories/3257023-fern-wifi-crack-best-er-for-windows-8-free-download
gittkamb 7b17bfd26b https://wakelet.com/wake/ZniuKojIETBXHrha1z1F-
A big thank you for your post.Much thanks again. Great.
https://shawmerchantgroup.medium.com
cadjam 7b17bfd26b https://trello.com/c/lokuvLjA/48-link-activationadvancesteel2019crack
hilltal 7b17bfd26b https://wakelet.com/wake/Wbsl-NlBe_8KlIbpg5Sq9
Не пропустіть кращі новинки кіно українською 2021 року link
bakell 7b17bfd26b https://trello.com/c/IB9RY7EN/26-hack-foxit-phantompdf-business-736321-multilingual-incl-patch-tea-cracked
sigrkee 7b17bfd26b https://coub.com/stories/3287494-befikre-movie-download-bluray-movie-exclusive
endjud 7b17bfd26b https://coub.com/stories/3472479-motu-patlu-king-of-kings-tamil-movie-download-top-in-utorrent
thomraf 7b17bfd26b https://www.cloudschool.org/activities/ahFzfmNsb3Vkc2Nob29sLWFwcHI5CxIEVXNlchiAgMCQipHYCAwLEgZDb3Vyc2UYgIDA0ICdgQsMCxIIQWN0aXZpdHkYgIDAgIuf0woMogEQNTcyODg4NTg4Mjc0ODkyOA
https://tapestry.tapad.com/tapestry/1?ta_partner_id=950&ta_redirect=https://ocrv.life/rv-repair-shop-lake-balboa-california
Excellent article. I'm going through some of these issues as well..
/
https://www.cropscience.bayer.ca/?setlanguage=en&returnUrl=https://ocrv.info/rv-repair-near-me
faypew 7b17bfd26b https://coub.com/stories/3231126-marques-houston-mh-install-full-album-zip
/
Can I just say what a comfort to discover somebody that genuinely knows what they are discussing on the net. You actually know how to bring a problem to light and make it important. More and more people ought to look at this and understand this side of your story. I was surprised you're not more popular given that you definitely possess the gift.
/holostyak-stb-2021
Найкращі фільми 2021 Золото 17 серия
https://sessionize.com/redirect/8gu64kFnKkCZh90oWYgY4A/?url=https://ocrv.vip/safeco-rv-collision-repair-shop-near-me
/
Everyone loves it when individuals come together and share thoughts. Great website, stick with it!
/
You have made some really good points there. I looked on the net to learn more about the issue and found most people will go along with your views on this website.
https://www.oic.or.th/sites/all/modules/pubdlcnt/pubdlcnt.php?file=http://ocrvcenter.net/workstar-collision-repair-shop-near-me
http://ww4.cef.es/trk/r.emt?h=www.ocrvmotorcoaches.com/rv-repair-shop-murrieta-california
https://dnevnik.ru/soc/moderation/abuse.aspx?link=http://ocrv.mobi/shuttle-truck-collision-repair-shop-near-me
etepeke 7b17bfd26b https://wakelet.com/wake/81Aqwj9K6yAvvp0peNXO4
collkel 7b17bfd26b https://seesaawiki.jp/monpcolrime/d/%28%28FREE%29%29%20Sarassalilin%2032%20Keygen%20License%20Pc%20Download%20%2ezip%20Full
orrediff ec2f99d4de https://wakelet.com/wake/aObxaEupPfaplbbJJoNqP
gilwate ec2f99d4de https://trello.com/c/3bh6Grph/62-final-microsoft-office-2016-crack-zip-pc-activation-64
I always spent my half an hour to read this web site's articles everyday along with a mug of coffee.|
https://anotepad.com/notes/qmfdw9xe
Have you ever thought about publishing an ebook or guest authoring on other websites? I have a blog based upon on the same topics you discuss and would love to have you share some stories/information. I know my viewers would value your work. If you are even remotely interested, feel free to shoot me an e mail.|
https://weshophere.ca/index.php?page=item&action=item_add
Iím amazed, I have to admit. Seldom do I come across a blog thatís both educative and interesting, and let me tell you, you've hit the nail on the head. The issue is something not enough people are speaking intelligently about. Now i'm very happy that I stumbled across this during my hunt for something concerning this.
https://na.eventscloud.com/emarketing/go.php?i=409508&e=&l=http://ocrvexperts.com/rv-repair-shop-monterey-park-california
Hi there to every body, it's my first go to see of this webpage; this weblog includes remarkable and truly good information designed for visitors.|
http://ttytcammy.vn/Default.aspx?tabid=120&ch=50105
Good article. I am facing many of these issues as well..
http://www.pcpitstop.com/offsite.asp?https://ocrv.me/motorhome-lighting-repair-near-me
I couldnít refrain from commenting. Exceptionally well written!
http://em.gohawaii.com/mtr40/c2.php?HVCB/26693011/218753/H/N/V/http://commercialrepairshop.com/semi-truck-repair-shop-near-me
https://www.autotriti.gr/news/preview_news.asp?home=webnews&url=https://ocrvexperts.com/rv-repair-shop-tustin-california
http://ads.cars.cz/adclick.php?bannerid=333&zoneid=237&source=&dest=https://ocrv.info/motorhome-countertop-repair-near-me
Muchos Gracias for your post.Really looking forward to read more. Really Cool.
https://slotxogame88.net/pg888th/
This excellent website certainly has all the information and facts I needed about this subject and didnít know who to ask.
https://autofans.joj.sk/api/rdr.php?key=Husqvarna+Ambassador&rdr=http://ocrvcenter.biz/shuttle-truck-collision-repair-shop-near-me
http://www.webexhibits.org/cs.html?url=https://ocrv.fun/rv-repair-shop-santa-ana-california
https://utrend.info/rvrepairnearme292093
http://www.canada.com/scripts/go.aspx?g=vancouversun&n=subscribe_link_relatedlinks&u=https://ocrv.rocks/rv-repair-shop-redlands-california
demeany 67426dafae https://coub.com/stories/4046072-patch-f4-meteor-gar-utorrent-professional-registration-full-version-pc-64
Hello there, I do think your blog could possibly be having browser compatibility problems. Whenever I take a look at your blog in Safari, it looks fine but when opening in Internet Explorer, it has some overlapping issues. I just wanted to give you a quick heads up! Other than that, fantastic website!
/
https://igert2011.videohall.com/to_client?target=https://ocrv.fun/rv-repair-shop-hermosa-beach-california
ranras 67426dafae https://coub.com/stories/4047984-jo-bole-so-nihaal-kickass-avi-subtitles-movie
/
nuridegu 67426dafae https://coub.com/stories/3975520-utorrent-fantasy-vii-crisis-core-mkv-exe-file-64-windows-full-version
Thank you for your post. Much obliged.
{https://www.youtube.com/watch?v=LBaXxiFLlFQ
fedlwer 67426dafae https://coub.com/stories/3981523-torrent-the-sleeping-dictionary-2003-subtitrare-ro-watch-online-subtitles-english
marigeri 67426dafae https://coub.com/stories/4027843-carbon-copy-cloner-5-1-15-5925-ed-for-activation-32-full-version-serial-macos
I would like to thank you for the efforts you've put in penning this site. I'm hoping to check out the same high-grade blog posts from you in the future as well. In fact, your creative writing abilities has encouraged me to get my own, personal blog now 😉
http://nudewwedivas.forumcommunity.net/m/ext.php?url=https://ocrv.fun/rv-repair-shop-burbank-california
wow, awesome article.Really thank you! Really Cool.
https://www.reddit.com/r/paintzoomreviews/comments/rq2yz8/paint_zoom_3000_paint_sprayer_demo_review_actual/
https://pixel.everesttech.net/2966/cq?ev_sid=105&ev_ltx=&ev_lx=297619603931&ev_crx=31464282863&ev_mt=p&ev_dvc=c&url=https://commercialvanrepairshop.com/semi-truck-dent-repair-shop-near-me
I will right away clutch your rss as I can't to find your e-mail subscription hyperlink or e-newsletter service. Do you've any? Please permit me recognise so that I could subscribe. Thanks.|
https://munksgaard-lara.technetbloggers.de/burlap-sacks-options-for-function-style-and-play-are-endless-1637944963
Thank you for every other fantastic article. Where else could anyone get that type of information in such a perfect approach of writing? I have a presentation next week, and I'm at the look for such information.|
http://husarria.eu/forums/users/holgersenbach33/
Can I simply just say what a comfort to uncover someone who truly knows what they're discussing over the internet. You definitely realize how to bring a problem to light and make it important. A lot more people really need to check this out and understand this side of your story. I was surprised you're not more popular since you surely have the gift.
https://www.payrollservers.us/sc/cookie.asp?sitealias=24858076&redirect=https://ocrv.biz/rv-repair-shop-van-nuys-california
I just could not go away your website prior to suggesting that I really loved the standard information a person provide for your guests? Is gonna be again frequently to inspect new posts|
http://yachtlab.spbstu.ru/forums/users/lucas43anthony/
Very neat blog post.Really thank you! Really Great.
https://spacecoastdaily.com/2022/02/the-best-herbal-testosterone-booster-which-test-is-the-best/
http://cta-redirect.ex.co/redirect?&web=http://ocrv.fun/rv-toilet-repair-near-me
What's up, just wanted to say, I enjoyed this post. It was funny.Keep on posting!
http://citycategories.com/directory/listingdisplay.aspx?lid=5511
There's definately a great deal to know about this issue. I like all of the points you've made.
https://www.vogel.com.cn/adlog.php?url=https://ocrvcenter.net/rv-repair-shop-palm-desert-california
Having read this I believed it was extremely informative. I appreciate you spending some time and energy to put this information together. I once again find myself personally spending a lot of time both reading and posting comments. But so what, it was still worthwhile!
https://garbagedomain.com
Your style is unique compared to other folks I have read stuff from. Thanks for posting when you've got the opportunity, Guess I will just bookmark this page.
https://barbados.org/al/?event=ad.logClick&adChannelID=7&accountID=76&adPlaceID=323&adCreativeID=0&adGroupID=&webAddress=http://ocrv.pro/delivery-truck-collision-repair-paint-shop-near-me-orange-county
Your style is really unique in comparison to other people I've read stuff from. Thank you for posting when you have the opportunity, Guess I will just bookmark this web site.
http://forum.jsettlers.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
Hey There. I found your blog using msn. This is a very well written article. I?ll make sure to bookmark it and return to read more of your useful information. Thanks for the post. I will certainly comeback.
https://cloud.gonitro.com/p/UaFQBRXiHGgnbhyvogpMzg
phebcla 31ebe8ef48 https://wakelet.com/wake/i0yWS-jmFg8MwMPj5UxXE
Найкращі фільми 2021 site
Не пропустіть кращі новинки кіно українською 2021 року z.globus-kino.ru
https://momsnboys.com/cgi-bin/at3/out.cgi?id=242&tag=toplist&trade=https://garbagedomain.com
Spot on with this write-up, I really believe that this amazing site needs a lot more attention. Iíll probably be returning to see more, thanks for the info!
https://asia.google.bj/url?rct=t&sa=t&url=https://garbagedomain.com
Hi, I do believe your site could be having browser compatibility problems. Whenever I take a look at your website in Safari, it looks fine however, when opening in Internet Explorer, it's got some overlapping issues. I just wanted to give you a quick heads up! Other than that, wonderful site!
http://xn--c1aitjcgk.xn--p1ai/bitrix/rk.php?goto=https://www.garbagedomain.com/
hannblos 31ebe8ef48 https://wakelet.com/wake/omCWVdr6h1o1j79ZrKX1c
Good post. I learn something totally new and challenging on sites I stumbleupon every day. It will always be helpful to read through content from other writers and use a little something from other websites.
http://www.surabayateak.com/__media__/js/netsoltrademark.php?d=www.https://www.garbagedomain.com/
fataran 31ebe8ef48 https://wakelet.com/wake/sNvRZ7CfD1jEn9qUZoiNN
You have made some good points there. I checked on the web for more info about the issue and found most people will go along with your views on this web site.
http://www.boosterforum.com/vote-374818-217976.html?adresse=https://www.garbagedomain.com&
janaind 31ebe8ef48 https://wakelet.com/wake/0cvlYhis5M_P3QJQC04qr
Wonderful article! We will be linking to this great post on our website. Keep up the great writing.
https://shinglas.ua/bitrix/redirect.php?goto=https://garbagedomain.com
https://europe.google.com.cy/url?q=j&rct=j&url=https://garbagedomain.com
Всі фільми новинки 2020 року онлайн українською в хорошій якості filmiwap.store
hugbri 31ebe8ef48 https://wakelet.com/wake/lhrpGpvOC5-Vt9LxTXUV9
This is the right web site for everyone who would like to find out about this topic. You know a whole lot its almost hard to argue with you (not that I actually would want toÖHaHa). You certainly put a fresh spin on a subject which has been discussed for a long time. Great stuff, just excellent!
https://www.thegreennest.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
safkei 31ebe8ef48 https://wakelet.com/wake/H9HhEaA-PGMxBphn-xnSQ
I know this website presents quality dependent content and additional stuff, is there any other web site which offers these data in quality?|
http://www.authorstream.com/smidtbowers7/
I like it when folks get together and share ideas. Great site, stick with it!|
https://acevedobritt92.bravejournal.net/post/2021/12/18/Top-Five-Best-Iphone-Endless-Runners
http://dtvpal.tv/__media__/js/netsoltrademark.php?d=garbagedomain.com
Hey I know this is off topic but I was wondering if you knew of any widgets I could add to my blog that automatically tweet my newest twitter updates. I've been looking for a plug-in like this for quite some time and was hoping maybe you would have some experience with something like this. Please let me know if you run into anything. I truly enjoy reading your blog and I look forward to your new updates.|
http://sxd.dongnai.gov.vn/lists/hiscounter/dispform.aspx?id=2245074&ContentTypeID=0x01003AC3E9B31087484C90C650786A0B5952
Way cool! Some very valid points! I appreciate you writing this post and also the rest of the website is really good.
https://affordableagility.com/cgi-bin/mcart/ares.cgi?ID=200947528&url=www.garbagedomain.com
Great blog post.Thanks Again. Will read on...
https://www.youtube.com/watch?v=-YD7oERwusM
Найкращі фільми 2021 Захар Беркут
Aw, this was a very nice post. Finding the time and actual effort to produce a top notch articleÖ but what can I sayÖ I procrastinate a lot and don't seem to get nearly anything done.
http://www.homepage.manhattanplace.com/__media__/js/netsoltrademark.php?d=https://garbagedomain.com/
http://dmsg.de/externerlink.php$?url=garbagedomain.com/
You're so awesome! I do not think I've read through anything like that before. So wonderful to find another person with some original thoughts on this subject. Seriously.. many thanks for starting this up. This web site is something that is needed on the internet, someone with a little originality!
https://www.txdot.gov/help/urlstatusgo.html?url=https://www.garbagedomain.com/
Great blog.Much thanks again.
https://www.youtube.com/watch?v=yd9lt_sB7Ww
http://frienddo.com/out.php?url=https://http://www.garbagedomain.com/
caylkers 00dffbbc3c https://coub.com/stories/4217742-blu-ray-s-in-watch-online-utorrent-free-mp4
xilsama 00dffbbc3c https://coub.com/stories/4345255-8-bit-inva-windows-utorrent-registration-zip-full-patch
Having read this I thought it was very enlightening. I appreciate you taking the time and effort to put this short article together. I once again find myself personally spending a lot of time both reading and commenting. But so what, it was still worth it!
http://heavyplumpers.com/cgi-bin/a2/out.cgi?link=tmx1x155x499843&u=https://www.yelp.com/biz/ocrv-center-yorba-linda/
I truly love your website.. Excellent colors & theme. Did you build this web site yourself? Please reply back as Iím hoping to create my very own blog and want to learn where you got this from or just what the theme is called. Appreciate it!
http://aspro.com.ua/bitrix/redirect.php?goto=https://www.pinterest.com/ocrvcenter//
This is a great tip particularly to those new to the blogosphere. Short but very accurate infoÖ Many thanks for sharing this one. A must read post!
https://www.questionpro.com//a/jsp/run/iframe.jsp?url=https3A2F2Fg.page/ocrvcenter
Greetings! Very useful advice in this particular post! It is the little changes that will make the greatest changes. Thanks a lot for sharing!
http://blackhistorydaily.com/black_history_links/link.asp?link_id=5&URL=https://www.yelp.com/biz/ocrv-center-yorba-linda/
Really enjoyed this blog article.Much thanks again. Want more.
https://slotxogame88.net/สล็อต-888
That is a really good tip especially to those fresh to the blogosphere. Short but very accurate informationÖ Thank you for sharing this one. A must read article!
http://fer.kgbinternet.com/webcams/offset.jsp?url=nextdoor.com/pages/ocrv-center-rv-truck-body-repair-paint-frame-fiberglass-sales/&linkpagina=&offsetvertic=62&offsetorizz=8&altezza=500&larghezza=648&nomecam=ISAVIG&citta=Savignano20sul20Rubicone&titolo1=La20spiaggia&titolo2=
http://nakedteenphoto.com/dtr/link.php?gr=1&id=39af34&url=https://youtube.com/watch?v=4EI8pQetwp8
http://blog.siol.net/agregat/redirect_post/?url=https://facebook.com/ocrvcenter/
http://a-kyu.oto9.net/shop/rank.cgi?mode=link&id=587&url=https://pinterest.com/ocrvcenter//
I blog often and I seriously thank you for your content. The article has truly peaked my interest. I'm going to bookmark your website and keep checking for new information about once per week. I opted in for your Feed too.
https://bbs.pku.edu.cn/v2/jump-to.php?url=counsellingrp.net/sito/index.php?option=com_phocaguestbook&view=phocaguestbook&id=1&Itemid=8&t=1880&limitstart=280
https://www.treasury.gov/cgi-bin/redirect.cgi/?https://elliottb59o0.blogaritma.com/5100046/a-review-of-chevy-g20-van-repair/
You are so awesome! I don't think I've read through something like that before. So nice to find someone with a few unique thoughts on this topic. Really.. thank you for starting this up. This web site is something that is needed on the internet, someone with some originality!
https://web.hcps.ptc.edu.tw/dyna/webs/gotourl.php?url=truckrentalshinkise.blogspot.com/2017/03
chaarya 219d99c93a https://coub.com/stories/4238731-utorrent-esic-form-105-l-book-pdf-zip
sashado 219d99c93a https://coub.com/stories/4289285-special-full-version-windows-torrent-zip-software-serial-key
thedisl 219d99c93a https://coub.com/stories/4350556-ricoh-aficio-mp-6001-driver-key-zip-cracked-utorrent
http://www.cobaev.edu.mx/visorLink.php?url=convocatorias/DeclaracionCGE2020&nombre=DeclaracióndeSituaciónPatrimonial2020&Liga=https://best-electric-toothbrush02839.blogsvila.com/7004261/not-known-details-about-rv-generator-repair-near-me
Itís hard to come by experienced people in this particular topic, but you sound like you know what youíre talking about! Thanks
https://www.treasury.gov/cgi-bin/redirect.cgi/?www.hector8l67e.bloggazzo.com/3867660/a-review-of-rv-service-near-me/
buttmon 219d99c93a https://coub.com/stories/4226431-professional-kaspersky-kts-kis-kav2019-v19-0-0-1088-trial-resetter-key-nulled-torrent
gavrvach 219d99c93a https://coub.com/stories/4263047-u-microsoft-office-full-version-32-crack-utorrent-pro
graieza 219d99c93a https://coub.com/stories/4344490-full-c-ofdutywwiidigital-ultimate-32bit-zip-serial
An intriguing discussion is definitely worth comment. I believe that you should publish more on this subject matter, it may not be a taboo subject but generally people don't talk about these topics. To the next! All the best!!
https://coolpot.stream/story.php?title=tor-scam-list#discuss
cahllaw 219d99c93a https://coub.com/stories/4215698-solution-ultimate-crack-rar-windows-torrent
kalakalo 219d99c93a https://coub.com/stories/4324539-full-drbabasahebambedkar-windows-32bit-activation-pro
Good day! I simply want to offer you a big thumbs up for your great information you have got right here on this post. I'll be coming back to your web site for more soon.
https://www.irs.lg.gov.ng/__media__/js/netsoltrademark.php?d=https://www.rvrepairgarakuno.blogspot.com/2017/01/rv-repair-near-me.html/
Having read this I believed it was rather enlightening. I appreciate you spending some time and effort to put this content together. I once again find myself personally spending way too much time both reading and leaving comments. But so what, it was still worthwhile!
http://www.sc.devb.gov.hk/TuniS/https://www.game-mun.com/forum/index.php?topic=10778.0/
https://www.rspcb.safety.fhwa.dot.gov/pageRedirect.aspx?RedirectedURL=www.papanluncur14.blogspot.com/2021/07/rv-electrical-repair-near-me-rv.html
billygeneismarketing.com
Very neat blog.Really thank you! Really Great.
https://victorylethbridge.ca/category/blog/page/10/
tamward 219d99c93a https://coub.com/stories/4305339-720p-veer-zaara-avi-watch-online-2k
billygeneismarketing.com
I blog often and I really appreciate your information. This article has truly peaked my interest. I will take a note of your website and keep checking for new information about once per week. I subscribed to your Feed as well.
https://bbs.cfish.idv.tw/link.php?url=https://garbagedomain.com
wadpasc d9ca4589f4 https://wakelet.com/wake/2GVI0syoXqG9MicEo7Zd3
janino d9ca4589f4 https://wakelet.com/wake/Tz8OA4Jre2KSNO4GIQT7o
Having read this I believed it was extremely informative. I appreciate you taking the time and effort to put this content together. I once again find myself spending a significant amount of time both reading and leaving comments. But so what, it was still worthwhile!
https://web28.werkbank.bayern-online.de/cgi-bin/forum/gforum.cgi?url=https://www.youtube.com/watch?v=yez3fy8eyec
aleetali d9ca4589f4 https://wakelet.com/wake/YQaewqanw7h0jBJ-9njpv
hathprem d9ca4589f4 https://wakelet.com/wake/5pYUoHmIvRJ-yylkrnY01
Aw, this was a very nice post. Finding the time and actual effort to produce a top notch articleÖ but what can I sayÖ I put things off a whole lot and don't manage to get nearly anything done.
http://www.petazon.com/trafficcounter.php?id=14808&url=https://garbagedomain.com/
Really informative article.Really thank you! Will read on...
https://www.google.co.tz/url?q=https://allpainting.ca
what is aricept aricept medication warnings for donepezil
https://videogamemods.com/members/parentmexico8/activity/220529/
Everything is very open with a really clear description of the issues. It was definitely informative. Your website is useful. Thanks for sharing!
http://images.google.co.ck/url?q=https://garbagedomain.com
Heya! I'm at work browsing your blog from my new iphone!Just wanted to say I love reading your blog and look forward to all your posts!Carry on the excellent work!
https://cutt.us/OZ2in
http://www.garbagedomain.com.isdownorblocked.com/ru
Right now it looks like BlogEngine is the top blogging platform out there right now. (from what I've read) Is that what you are using on your blog?|
https://public.sitejot.com/faganzimmerm.html
Pretty great post. I just stumbled upon your blog and wished to say that I've truly loved browsing your blog posts. In any case I will be subscribing to your rss feed and I'm hoping you write once more soon!|
https://www.click4r.com/posts/g/3015269/watches-a-good-endless-value
When I originally commented I clicked the "Notify me when new comments are added" checkbox and now each time a comment is added Iget several e-mails with the same comment.Is there any way you can remove people from that service?Thanks a lot!
http://www.authorstream.com/SienaMcdaniel/
https://www.casmokershelpline.info/__media__/js/netsoltrademark.php?d=https://garbagedomain.com/
Great article. I am dealing with many of these issues as well..
http://google.com.gi/url?sa=t&url=garbagedomain.com/
I loved as much as you will receive carried out right here.
The sketch is tasteful, your authored material stylish.
nonetheless, you command get got an edginess over that you wish be delivering the following.
unwell unquestionably come more formerly again since exactly
the same nearly a lot often inside case you shield
this hike.
Have a look at my web blog - bola88
Hello, There's no doubt that your website might be having web browser compatibility problems. Whenever I take a look at your website in Safari, it looks fine however, when opening in I.E., it has some overlapping issues. I just wanted to give you a quick heads up! Aside from that, excellent website!
http://cruzgaxyy.actoblog.com/12064060/the-rv-body-repair-near-me-awards-the-best-worst-and-weirdest-things-we-ve-seen
http://brandonsun.com/s?action=editReg&rurl=https://ocrvcenter.info
This is a topic that's near to my heart... Take care! Where are your contact details though?
http://aldoventures.com/__media__/js/netsoltrademark.php?d=shoponline03456.bloginwi.com/42979082/why-you-should-forget-about-improving-your-rv-body-repair-near-me
Greetings! Very useful advice in this particulararticle! It is the little changes which will make the greatest changes.Thanks for sharing!
https://www.pearltrees.com/nathaliaolson/item432940563
Thank you for your blog.Much thanks again. Much obliged.Loading...
https://helloblacks.wordpress.com
Great blog article.Really looking forward to read more. Much obliged.
https://superslot888.net/
http://www.lotus-europa.com/siteview.asp?page=https://chamberofcommerce.com/united-states/california/yorba-linda/auto-repair/1340797506-ocrv-center-rv-repair-rv-remodeling
http://www.hachimantaishi.com/click3/click3.cgi?cnt=c5&url=https://www.ocrvandtrucks.com/
http://www.pahu.de/url?q=https://rvcollisionrepairpaintshop.com/
Great post. I'm experiencing many of these issues as well..
https://elahmad.com/url.php?url=https://www.ocrv.art/
Im grateful for the post.Thanks Again. Really Cool.
https://superslot888.net/
Hi there! This post couldnít be written any better! Looking at this post reminds me of my previous roommate! He always kept talking about this. I am going to forward this article to him. Fairly certain he's going to have a very good read. I appreciate you for sharing!
http://zopflex.com/wl/es/lb/blog/?trackingdomain=bookmarkrange.com/story9251614/ocrv-fleet-services-commercial-truck-collision-repair-paint-shop
Very good blog.Thanks Again. Really Cool.
https://slotxogame88.net/818king/
Pretty! This was an extremely wonderful article. Many thanks for supplying these details.
https://ar.paltalk.com/client/webapp/client/External.wmt?url=https://youtube.com/watch?v=tzit_qha6jk
Hey, thanks for the article post.Really thank you! Cool.
https://doodleordie.com/profile/restoration09
http://tharp.me/?url_to_shorten=https://juicycalls.com/
I couldnít resist commenting. Very well written!
http://historictraveler.com/__media__/js/netsoltrademark.php?d=shop-online74074.ampblogs.com/What-the-Best-RV-Body-Repair-Near-Me-Pros-Do-and-You-Should-Too--43846182
Thanks for sharing your thoughts about สล็อตเว็บตรง.Regards
https://firsturl.de/4y3RbvF
Very nice post. I absolutely appreciate this site. Keep it up!|
https://pridgensteele3.bravejournal.net/post/2022/02/08/What-Is-The-Highly-Recommended-Registry-Cleaning-Solution
Hi every one, here every person is sharing these kinds of experience, therefore it's fastidious to read this weblog, and I used to pay a visit this web site everyday.|
http://git.newslab.iith.ac.in/bentsen71lindhardt
Hello friends, how is all, and what you wish for to say concerning this paragraph, in my view its truly awesome designed for me.|
https://abdelgwad-hamida.com/members/tilleymccarty86/activity/248782/
https://www.e-tsudoi.com/redirect.php?url=https://www.spokanevalleywebdesign.com
http://qscience.com/locale/redirect?redirectItem=http://marketingpostfalls.com
Thanks-a-mundo for the article.Thanks Again. Really Great.
https://s789.online/
Terrific post but I was wondering if you could write a litte more on this subject? I'd be very thankful if you could elaborate a little bit more. Cheers!|
https://mybookmark.stream/story.php?title=latest-games-for-ios-and-android-users-4#discuss
I've been browsing on-line more than 3 hours today, but I never discovered any attention-grabbing article like yours. It is lovely value enough for me. In my opinion, if all webmasters and bloggers made excellent content as you did, the net shall be much more useful than ever before.|
https://www.bandlab.com/roman470
Greetings from Florida! I'm bored to tears at work so I decided to check out your blog on my iphone during lunch break. I enjoy the info you present here and can't wait to take a look when I get home. I'm amazed at how fast your blog loaded on my cell phone .. I'm not even using WIFI, just 3G .. Anyhow, very good site!|
http://www.teknallsnc.com/index.php?option=com_k2&view=itemlist&task=user&id=3814735
You need to take part in a contest for one of the finest websites on the web. I'm going to highly recommend this web site!
https://golfselect.com.au/redirect?activitytype_cd=web-link&course_id=2152&tgturl=https://passwordrecoverysoftwarez47866.blogpixi.com/9572050/sage-advice-about-rv-body-repair-near-me-from-a-five-year-old
Very quickly this web page will be famous among all blog people, due to it's pleasant content|
https://www.brownbook.net/account/profile/4684329
https://georgewbushlibrary.smu.edu/exit.aspx?url=https://www.youtube.com/watch?v=x4oj4fb_l7m
http://bostonpocketpc.com/ct.ashx?url=https://www.reviewnearme.com
happarm 538a28228e https://coub.com/stories/4358486-greys-ana-dubbed-utorrent-utorrent-film-watch-online-watch-online-dts
janealbi 538a28228e https://coub.com/stories/4265721-skymedi-fix-16gb-32bit-cracked-registration-download-full
lavext 538a28228e https://coub.com/stories/4309555-32-solucionario-ingenieria-termodinamica-jones-dugan-rar-patch-windows-activator
orscrai 538a28228e https://coub.com/stories/4328950-patron-mutlu-son-istiyor-full-2k-watch-online-watch-online-x264-4k-full
taiana 538a28228e https://coub.com/stories/4265604-windows-ctc-601-flash-crack-download-license
Hurrah, that's what I was searching for, what a material! existing here at this web site, thanks admin of this site.|
https://muabs.com/profile/asif678/
ancella 538a28228e https://coub.com/stories/4368460-virtuaguy-mo-pc-cracked-software-64bit-zip
elezak 538a28228e https://coub.com/stories/4316428-avi-c-of-juarez-bound-in-blood-razor1911-maxspeed-game-hack-password-dubbed-movies-kickass-2k
marwyn 538a28228e https://coub.com/stories/4325980-agile-velopment-scrum-ken-schwaber-36-book-full-utorrent-epub
fablenz 538a28228e https://coub.com/stories/4214608-software-aim-cfg-torrent-free-exe
https://www.viidii.info/?www.ppcpostfalls.com/
chilbir 538a28228e https://coub.com/stories/4234022-biology-by-stephen-wicki-utorrent-book-rar-full-version-epub
kalhal 538a28228e https://coub.com/stories/4219782-fsx-steam-x64-registration-zip-cracked
I love what you guys are up too. This sort of clever workand exposure! Keep up the wonderful works guys I've incorporated you guys tomy personal blogroll.
https://jaydenjamesbarnard.wordpress.com/2022/03/15/information-you-have-to-find-out-about-the-attributes-of-steel-doors/
ulbrheli 538a28228e https://coub.com/stories/4258739-signingnatur-exe-key-windows-serial-free-32-torrent
meeging 538a28228e https://coub.com/stories/4366398-mongol-the-rise-of-g-1080p-watch-online-dubbed-full-dvdrip-mp4
meeging 538a28228e https://coub.com/stories/4366398-mongol-the-rise-of-g-1080p-watch-online-dubbed-full-dvdrip-mp4
marckaff 538a28228e https://coub.com/stories/4278350-karafun-karaoke-12-windows-rar-license-32bit-download-129311
Hi, I think your website could be having internet browser compatibility problems. When I take a look at your blog in Safari, it looks fine however when opening in Internet Explorer, it's got some overlapping issues. I merely wanted to give you a quick heads up! Aside from that, great site!
http://www.grancanariamodacalida.es/ver_video_popup.php?video=http://www.codymarketing.com/
Thanks for sharing your thoughts about meta_keyword. Regards|
https://gfycat.com/settings/account
Really appreciate you sharing this blog article.Really looking forward to read more. Great.
https://famouslinkuae.com/
You should be a part of a contest for one of the best websites on the net. I am going to recommend this blog!
&date=201810
Hello! This post couldn't be written any better! Reading this post reminds me of my good old room mate! He always kept chatting about this. I will forward this post to him. Fairly certain he will have a good read. Thanks for sharing!|
https://www.atlasobscura.com/users/9bd2862c-5e13-4449-8283-45ad15e85c1f
If you are going for finest contents like myself, only pay a quick visit this web site everyday for the reason that it provides feature contents, thanks|
https://notes.io/Fxed
I value the blog post. Want more.
https://drive.google.com/file/d/13IajcSSVfnZ01SX7hPugJLwJbY6NyByn/view?usp=sharing
https://web.hcps.ptc.edu.tw/dyna/webs/gotourl.php?url=www.ocrvcenter.mobi/medical-truck-collision-repair-paint-shop-near-me-orange-county
how do you take zithromax when to take zithromax z pak used for uti
https://braggal.com/braggal-members/treedoubt22/activity/2909/
Very good information. Lucky me I discovered your website by chance (stumbleupon). I've book marked it for later!
https://www.historyhub.history.gov/external-link.jspa?url=https://www.ocrvluxurycoaches.com/rv-repair-shop-hidden-hills-california
You completed some nice points there. I did a search on the theme and found a good number of people will agree with your blog.
https://rohitink.com/2021/12/22/e-commerce-web-development/
I really like and appreciate your article post.Thanks Again. Really Cool.
https://raiser.network/
What's up colleagues, how is the whole thing, and what you want to say regarding this post, in my view itsreally awesome designed for me.
https://luke-sutton.co.uk/
http://libproxy.chapman.edu/login?url=https://www.commercialvanrepairshop.com/gmc-high-top-van-repair-shop-near-me/
Hello there! I could have sworn Iíve been to your blog before but after looking at a few of the posts I realized itís new to me. Anyways, Iím certainly pleased I found it and Iíll be bookmarking it and checking back frequently!
http://mambasana.ru/redir/?ocrvcenter.mobi/rv-repair-shop-twentynine-palms-california
larrlor b8d0503c82 https://coub.com/stories/4725690-utorrent-henne-kelu-ninnaya-golu-kannada-police-news-paper-34-64bit-zip-software-registration-pc
judeula b8d0503c82 https://coub.com/stories/4637267-full-version-el-r-scrolls-skyrim-1-2-14-0-trainer-registration-nulled-file-torrent-64-zip
Itís hard to come by well-informed people in this particular topic, but you seem like you know what youíre talking about! Thanks
http://www.noexcuselist.com/li/?url=https://www.ocrvcenter.org/airport-bus-collision-repair-shop-near-me
kaegar b8d0503c82 https://coub.com/stories/4522085-tera-pyar-hookah-bar-registration-32bit-pc-zip-free
ectoinri b8d0503c82 https://coub.com/stories/4645687-nero-platinum-pc-final-exe-crack-activation
blaaobr b8d0503c82 https://coub.com/stories/4642941-eplanp8dataportal-torrent-pc-nulled-final-activation-rar-full
habire b8d0503c82 https://coub.com/stories/4545757-bs-pd-5500-32bit-final-registration-utorrent-rar-cracked
wakhar b8d0503c82 https://coub.com/stories/4540872-creo-elements-direct-mo-iso-ultimate-64bit-free-download
Hi there! Do you know if they make any plugins to safeguard against hackers? I'm kinda paranoid about losing everything I've worked hard on. Any tips?|
http://ufotech.com.vn/members/manahil-khan.905624/
This post is worth everyone's attention. Where can I find out more?|
https://ignitiondeck.com/id/dashboard/?backer_profile=81800
Iím impressed, I must say. Seldom do I encounter a blog thatís equally educative and interesting, and let me tell you, you've hit the nail on the head. The issue is something not enough men and women are speaking intelligently about. Now i'm very happy that I came across this during my search for something relating to this.
https://www.he-web.com/rank.cgi?mode=link&id=6111&url=https://dyerbilt.com/
Looking forward to reading more. Great blog.Really thank you! Cool.
https://amb19.com/
{
https://www.vingle.net/Majid600
Very nice article. I definitely love this site. Keep it up!
http://wilsonlearning.com/?URL=https://spokanevalleymarketing.com/
cheap sildenafil sildenafil side effects long term
Wow, this article is nice, my younger sister is analyzing such things, thus I am going to let know her.|
https://cutt.us/LaGm5
Thank you for some other wonderful post. The place else could anybody get that type of info in such a perfect manner of writing? I have a presentation next week, and I'm on the search for such information.|
https://suzuri.jp/alikhan
https://publishing.brookes.ac.uk/?URL=www.ocrv.us/rv-repair-shop-moreno-valley-california
jeffreyw25a3.mpeblog.com/25454513/inexpensive-options-to-classic-vehicle-body-fix-paintless-dent-repair-service-location-paint-restore
wonderful put up, very informative. I wonder why the opposite experts of this sector don't understand this. You must continue your writing. I am confident, you've a huge readers' base already!|
http://www.bcsnerie.com/members/burkeburke43/activity/1346981/
What's up to every single one, it's actually a good for me to pay a quick visit this website, it includes valuable Information.|
https://linkvault.win/story.php?title=new-seniors-new-years-resolutions-5#discuss
I loved your article post.Much thanks again. Really Cool.
https://www.techniccar.com/wp-includes/agen-bola-sbobet/
Thank you for your blog.Much thanks again. Fantastic.
https://www.forestskin.com/
Bardzo interesujące informacje! Idealnie to, czego szukałem maseczka jednorazowa cena maseczka jednorazowa cena.
https://helloblacks.wordpress.com
takqua 220b534e1b https://www.kaggle.com/kututisi/cross-court-tennis-2-apk-crack-bested-16
rawluzzy 220b534e1b https://www.kaggle.com/tranneulire/luckhnowi-ishq-movie-download-in-hi-cracked
Hey, I think your site might be having browser compatibility issues. When I look at your website in Ie, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, fantastic blog!|
https://www.boredpanda.com/author/majedsheih721/
Great post however I was wondering if you could write a litte more on this topic? I'd be very grateful if you could elaborate a little bit further. Bless you!|
https://hollis-mccain.blogbright.net/country-kitchen-design-add-warmth-and-charm-to-your-kitchen-1641601474
Im grateful for the post.Much thanks again. Keep writing.
https://www.news-eventsmarketing.com/post/the-history-of-st-patricks-day
Howdy! Do you use Twitter? I'd like to follow you if that would be ok. I'm undoubtedly enjoying your blog and look forward to new updates.|
http://hiphopinferno.com/user/Khiladi097
Hey, I think your website might be having browser compatibility issues. When I look at your website in Ie, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, fantastic blog!|
http://git.newslab.iith.ac.in/dohn92dohn
ganarab df76b833ed https://www.kaggle.com/visveranchtal/sandisk-rescuepro-deluxe-v5001-portable
chryhug df76b833ed https://www.kaggle.com/notukiti/install-m3u8-downloader-converter-v3-0-0-u
nicbali df76b833ed https://www.kaggle.com/liranhandfo/wondershare-pdfelement-6-6-1-3295-c-top
jesjasp df76b833ed https://www.kaggle.com/pricalpsychin/cinthol-confidence-commercial-full-full
http://libregraphicsworld.org/?URL=jsminjuryfirm.com/blog
amamar df76b833ed https://www.kaggle.com/contingtaja/galat-baat-hai-full-link-video-song-1080p
kaffpan df76b833ed https://www.kaggle.com/tetureto/tamil-dubbed-movies-free-download-i-hot
roslyv df76b833ed https://www.kaggle.com/sgenamomro/extra-quality-stellar-phoenix-cd-dvd-data-recover
marjnea df76b833ed https://www.kaggle.com/taumimaba/maya201264bitproductkeyandxforcekeygenra-hanfel
ysobqad df76b833ed https://www.kaggle.com/diasinciamu/automation-anywhere-enterprise-crac-hot
Fantastic article post.Thanks Again. Fantastic.
https://www.slinkywebdesign.com.au/
yeniles df76b833ed https://www.kaggle.com/erinfacmons/upd-amazing-photo-editor-serial-number
What's Going down i'm new to this, I stumbled upon this I have discovered It absolutely useful and it has helped me out loads. I am hoping to give a contribution & aid different users like its aided me. Good job.|
http://bvkrongbong.com/Default.aspx?tabid=120&ch=64278
halthaw df76b833ed https://www.kaggle.com/kiestimlocky/biologia-de-las-plantas-raven-pdf-e-exclusive
Quality articles or reviews is the crucial to be a focus for the users to visit the web site, that's what this web page is providing.|
http://husarria.eu/forums/users/harringtonwoods4/
Ridiculous story there. What occurred after? Thanks!|
https://boldorganizing.org/forums/users/riisedemir8/
I don't know if it's just me or if perhaps everybody else experiencing problems with your website. It appears like some of the text in your content are running off the screen. Can somebody else please comment and let me know if this is happening to them too? This might be a issue with my browser because I've had this happen previously. Thank you|
http://trungtamytethanhtri.vn/Default.aspx?tabid=120&ch=252579
Hi there! This is my first visit to your blog! We are a collection of volunteers and starting a new initiative in a community in the same niche. Your blog provided us beneficial information to work on. You have done a outstanding job!|
https://king-bookmark.stream/story.php?title=enjoy-android-phones-under-contract-mobile-phone-deals#discuss
I value the blog post.Really looking forward to read more. Cool.
https://akwam.to/
edwabern df76b833ed https://www.kaggle.com/gwenenrecmost/link-salaam-namaste-movie-1080p-torrent
https://www.davidgiard.com/ct.ashx?url=http://www.jsminjuryfirm.com/paralysis-injury-lawyer
Hello, always i used to check weblog posts here in the early hours in the dawn, since i love to find out more and more.|
https://notes.io/Ac76
Aw, this was a really nice post. Taking the time and actual effort toproduce a great article... but what can I say... I put things off a whole lot and neverseem to get nearly anything done.
https://www.reformasreimar.es
Very informative post.Really thank you! Will read on...
https://exipurereviews.blob.core.windows.net/exipure/Exipure-Bbb-Reviews-Complaints.html
Hi there, of course this paragraph is really pleasant and I have learned lot of things from it concerning blogging. thanks.|
http://alasiilat.com/index.php?qa=user&qa_1=brink56gade
Great info! I'll be back for more great content. Love reading this stuff.
https://www.funfacts.com
You could certainly see your enthusiasm within the work you write. The sector hopes for even more passionate writers such as you who aren't afraid to mention how they believe. Always follow your heart.
https://itsmyurls.com/budgetantenna
Good article. I will be dealing with some of these issues aswell..
https://visual.ly/users/madelynlara/portfolio
carlrayd 89fccdb993 https://www.guilded.gg/migefirmos-Spartans/overview/news/x6gYNw8R
phecol 89fccdb993 https://www.guilded.gg/docreipredons-Mavericks/overview/news/vR13QpM6
I am sure this paragraph has touched all the internet people, its really really good piece of writing on building up new blog.
https://openarticlesubmission.com/one-big-party-dallas-delivers-the-perfect-party-rentals/
Wow, great blog.Much thanks again. Cool.
https://www.youtube.com/watch?v=th_AbCOsRts
leyilly 89fccdb993 https://www.guilded.gg/sumidenjacks-Crew/overview/news/B6Z033AR
kurloli 89fccdb993 https://www.guilded.gg/schotmorobnis-Flyers/overview/news/16YV8Wny
wavayl 89fccdb993 https://www.guilded.gg/dinceheartplas-Highlanders/overview/news/xypL29Ey
fordjan 89fccdb993 https://www.guilded.gg/rigreausquarkis-Vikings/overview/news/16n49oOR
uraquil f23d57f842 https://www.guilded.gg/terppemawoods-Hawks/overview/news/7lxYjZz6
edelkall f23d57f842 https://www.guilded.gg/segalduvis-Mavericks/overview/news/zy43MZz6
frazyko f23d57f842 https://www.guilded.gg/labgimensparks-Aces/overview/news/bR9pGOey
tainay f23d57f842 https://www.guilded.gg/unmugymus-Greyhounds/overview/news/gy8AJ4NR
A big thank you for your article.Much thanks again. Fantastic.
https://www.youtube.com/watch?v=PvvbtYq7928
eliasafa f23d57f842 https://www.guilded.gg/paydilalus-Cubs/overview/news/NyEgg3Gl
heafea f23d57f842 https://www.guilded.gg/masxepinos-Rockets/overview/news/r6BpGQ1R
abrapa f23d57f842 https://www.guilded.gg/labgimensparks-Aces/overview/news/vR1njE5l
It's fantastic that you are getting thoughts from this paragraph as well as from our dialogue made atthis time.
http://getconrad.xyz/story.php?id=16344
weddwas f23d57f842 https://www.guilded.gg/alicsiostels-League/overview/news/7lxYgWW6
I don’t even know the way I stopped up here, however I thought this submit was great. I don’t know who you are however definitely you’re going to a famous blogger should you are not already. Cheers!
https://www.kiva.org/lender/ethan7451
celynerv f23d57f842 https://www.guilded.gg/esrifilos-Mercenaries/overview/news/7lxw2jYR
I'm very happy to discover this page. I need to to thank you for your time just for this fantastic read!! I definitely loved every bit of it and I have you bookmarked to look at new information on your web site.|
http://yachtlab.spbstu.ru/forums/users/pappasgreenwood50/
What's Happening i'm new to this, I stumbled upon this I have found It absolutely useful and it has aided me out loads. I'm hoping to contribute & help different customers like its aided me. Good job.|
https://linkvault.win/story.php?title=iphone-gaming-explosion#discuss
dargius f23d57f842 https://www.guilded.gg/redylifans-Owls/overview/news/9yWVeEX6
yemvit f23d57f842 https://www.guilded.gg/mateddersnas-Wizards/overview/news/X6QPY53l
You really make it seem so easy with your presentation but I find this topic to be really something that I think I would never understand. It seems too complex and extremely broad for me. I'm looking forward for your next post, I will try to get the hang of it!|
https://reda.sa/members/stuart32ebbesen/activity/689395/
Excellent web site. Lots of useful information here. I'm sending it to a few buddies ans additionally sharing in delicious. And naturally, thanks for your sweat!|
https://pbase.com/topics/wallbrady5/best_wordpress_plugins_for_t
berhyr f23d57f842 https://www.guilded.gg/sandcenpaheds-Mob/overview/news/JRNdGNZ6
peanhali f23d57f842 https://www.guilded.gg/deftynencbes-Hawks/overview/news/xypDKQGy
penhelk f23d57f842 https://www.guilded.gg/pregquitinboas-Wanderers/overview/news/Jla8MzOR
karicere f23d57f842 https://www.guilded.gg/chemdtohejos-Senators/overview/news/V6XbgaoR
Really when someone doesn't be aware of after that its up to other people that they willhelp, so here it takes place.
https://www.collegethink.com/uemsconnect/members/quiltsock35/activity/198423/
ilaudo f23d57f842 https://www.guilded.gg/inapskydors-Highlanders/overview/news/9RVYnDwy
tinkrand f23d57f842 https://www.guilded.gg/mefecttares-Warlocks/overview/news/Yyrank56
I dugg some of you post as I thought they were extremely helpful extremely helpful
http://ericampire.xyz/story.php?id=14750
nantdee f23d57f842 https://www.guilded.gg/kutebernleths-Cardinals/overview/news/bR9pvMPy
siggior f23d57f842 https://www.guilded.gg/staronpredars-Cobras/overview/news/A6jvZKd6
bennsant f23d57f842 https://www.guilded.gg/propeckeytus-Legion/overview/news/qlDDGnnl
papijas f23d57f842 https://www.guilded.gg/piwelzeiters-Raiders/overview/news/x6geZV8R
This is the right site for everyone who wishes to find out about this topic. You realize so much its almost hard to argue with you (not that I really will need toÖHaHa). You definitely put a new spin on a subject that has been written about for decades. Great stuff, just great!
/
braale f23d57f842 https://www.guilded.gg/dantobihes-Heroes/overview/news/9loe4mNy
antberw 6be7b61eaf https://trello.com/c/svatBZEy/36-link-grand-theft-auto-vice-city-underground
demrafa 6be7b61eaf https://trello.com/c/tjMaeYr4/46-top-tc7-leithold-calculus-book-torrent19
pemder 6be7b61eaf https://trello.com/c/36DbdLFZ/58-break-through-the-silence-martin-garrix-mp3-download-hot-320kbps
keylcahl 6be7b61eaf https://trello.com/c/nKuwzx0k/41-80111-n-wlan-adapter-driver-yanysyb
reiljac 9c0aa8936d https://murmuring-waters-11999.herokuapp.com/Crysis2MaximumEditionPROPHET-2018-no-survey.pdf
ginephy 9c0aa8936d https://stormy-sierra-31395.herokuapp.com/The-Sims-2-FreeTimevitalityplayabletoday-hack-tool-download.pdf
farydar cbbc620305 https://marketplace.visualstudio.com/items?itemName=timocdeude.HOT-Ispring-Pro-With-Crack-Torrent
vienamil cbbc620305 https://marketplace.visualstudio.com/items?itemName=atesanho.Astra-Image-PLUS-553-TOP
This story is going to explore that issue in some detail.
https://korbentaylor.yooco.org/
I really like and appreciate your article.Really looking forward to read more. Really Cool.
https://medium.com/kelvin-kaemingk/about
I do not even know how I ended up right here, but I believed this submit was once good.I don't recognize who you're but certainly you'regoing to a well-known blogger when you are not already. Cheers!
https://helloblacks.wordpress.com
http://www.wrasb.gov.tw/opennews/opennews01_detail.aspx?nno=2014062701&return=www.prept196302479.blognody.com/9983850/selecting-an-car-system-repair-shop/
I was recommended this blog by my cousin. I'm not sure whetherthis post is written by him as no one else know such detailed about my problem.You are incredible! Thanks!
https://www.swdao.org/products/alpha-portfolio
Excellent web site you have got here.. It's difficult to find good quality writing like yours nowadays. I really appreciate individuals like you! Take care!!|
https://coolpot.stream/story.php?title=building-your-ideal-practice-from-creativity-to-completion#discuss
Thanks for every other fantastic post. The place else may just anyone get that kind of info in such a perfect method of writing? I've a presentation subsequent week, and I'm on the look for such info.|
https://www.crewministries.com/members/lancaster18chappell/activity/148065/
I'm very happy to find this page. I want to to thank you for ones time due to this fantastic read!! I definitely really liked every bit of it and I have you saved as a favorite to look at new things in your blog.|
http://yourumla.com/index.php?qa=user&qa_1=parsons45watts
You are so interesting! I do not suppose I've truly read through something like this before. So nice to find someone with a few genuine thoughts on this topic. Seriously.. many thanks for starting this up. This website is one thing that's needed on the internet, someone with a bit of originality!
https://advtest.exibart.com/adv/adv.php?id_banner=7201&link=http://wdir1.com/link/217954/ocrv-fleet-services-commercial-truck-collision-repair-paint-shop/
whoah this blog is excellent i love studying your posts.Keep up the great work! You already know, lots of individuals are hunting round for this info, youcould aid them greatly.
https://milkyway.cs.rpi.edu/milkyway/show_user.php?userid=2582398
Major thanks for the blog.Really thank you! Much obliged.
https://www.youtube.com/watch?v=MK8AxflmUMQ
The second biggest sporting occasion in the United Statesis the March Madness basketball tournament that takes location every spring.
https://helloblacks.wordpress.com
Hi there to every body, it's my first go to see of
this weblog; this web site carries amazing and in fact excellent data designed for readers.
Here is my blog ... airline tickets best price
http://esso.zjzwfw.gov.cn/opensso/UI/Logout?goto=https://laju-nuertingen.de/guestbook?start=3280
veredmo 9ff3f182a5 https://www.kaggle.com/code/sporacualbou/bengali-movie-manorama-six-feet-und-exclusive
sadgian 9ff3f182a5 https://www.kaggle.com/code/amkorpico/saala-khadoos-movie-download-1080p-movie-dardia
kafgly 63b95dad73 https://marketplace.visualstudio.com/items?itemName=tournamen.Marathiserialhomeministertitlesong
tarferm 63b95dad73 https://marketplace.visualstudio.com/items?itemName=subsmata-i.Notes-Donate-V729-Crack-BESTed-Latest
owindanc 63b95dad73 https://marketplace.visualstudio.com/items?itemName=compadre.Office-20132019-C2R-Install-V171516-B2-Lite-Micros-FULL
healralf 63b95dad73 https://marketplace.visualstudio.com/items?itemName=ravelee.Coldplay-Greatest-Hits-2011
decakafl 63b95dad73 https://marketplace.visualstudio.com/items?itemName=2anbuve-tsu.Weird-Science-A-Giantess-Tale
aleeott 63b95dad73 https://marketplace.visualstudio.com/items?itemName=larizia.Mohabbatein-Full-Movie-With-Malay-Subtitles-Downloadl-savchuc
Hello, I log on to your blog daily. Your story-telling style is witty, keep up the good work!|
https://westernt2p.ca/members/beasleynikolajsen6/activity/934149/
manhal 63b95dad73 https://marketplace.visualstudio.com/items?itemName=gfrsdgsdf.WORK-Nitrobake-Cinema-4d-Download-Pc
Hi there! I just wanted to ask if you ever have any problems with hackers? My last blog (wordpress) was hacked and I ended up losing months of hard work due to no back up. Do you have any solutions to protect against hackers?|
http://www.bcsnerie.com/members/graceconnolly8/activity/1201024/
clequed 63b95dad73 https://marketplace.visualstudio.com/items?itemName=nisrafupe.KGB-Key-Logger-454-Serial-TIMETHIEF-121-Serial-Key-Keyg-talwash
Wow that was strange. I just wrote an very long comment but after I clicked submit my comment didn't show up. Grrrr... well I'm not writing all that over again. Anyhow, just wanted to say fantastic blog!|
https://bookmarkingworld.review/story.php?title=iphone-5-did-not-premiere-are-consumers-disappointed-or-are-they-happy-with-4s#discuss
Great information. Lucky me I recently found your blog by accident (stumbleupon). I've book marked it for later!|
http://al-frasha.com/index.php?qa=user&qa_1=vancerose71
Great site you have here.. It's difficult to find quality writing like yours these days. I truly appreciate people like you! Take care!!|
https://cipres.fogbugz.com/default.asp?pg=pgPublicView&sTicket=696523_f5oecal1
queral 63b95dad73 https://marketplace.visualstudio.com/items?itemName=mortifer.BEST-Hulya-Kocyigit-Seks-Film-Sahnesigolkes
Quality posts is the key to invite the viewers to visit the website, that's what this web page is providing.|
https://kartalescortt.net/author/juel88mathews/
What's Happening i am new to this, I stumbled upon this I have found It positively helpful and it has aided me out loads. I hope to contribute & assist other users like its helped me. Great job.
https://www.reformasdecocinazaragoza.com
Heya i'm for the primary time here. I found this board and I
find It truly helpful & it helped me out a lot. I hope to give something back and help others
like you helped me.
Take a look at my homepage - fly tickets
Thanks to my father who stated to me concerning this blog,this blog is truly remarkable.
https://www.reformasprodicozaragoza.com
I'm gone to tell my little brother, that he should also pay a visit this webpage on regular basis
to take updated from most recent gossip.
Also visit my blog - airline tickets
Really informative post.Really looking forward to read more. Great.
https://pl.sonnik.wiki/znaki-i-przesady/
I value the post.Thanks Again. Awesome.
https://trustclub.org/
Hey there! I could have sworn I've been to this site before but after checking through some of the post I realized it's new to me. Nonetheless, I'm definitely happy I found it and I'll be bookmarking and checking back frequently!|
https://saveyoursite.win/story.php?title=pros-and-cons-in-the-iphone-5#discuss
Hi! Someone in my Myspace group shared this site with us so I came to give it a look. I'm definitely enjoying the information. I'm bookmarking and will be tweeting this to my followers! Wonderful blog and amazing design and style.|
https://wardmccallum51.werite.net/post/2022/01/30/Cookbook-And-Food-Magazine-Addictions,-Part-Deux,-Hardcover
Hi there all, here every one is sharing such experience, therefore it's good to read this web site, and I used to pay a visit this web site every day.|
http://be2concept.be/index.php?qa=user&qa_1=mcnamaramcintyre08
sildenafil 85
https://bookmarking.win/story.php?title=chocolate-viet-nam#discuss
I am truly thankful to the owner of this web site who has shared this fantastic piece of writing at at this time.|
http://answerpail.com/index.php?qa=user&qa_1=mouridsenkatz7
Thanks so much for the article.Much thanks again. Keep writing.
https://trustclub.org/
Excellent blog you have got here.. It’s hard to find quality writing like yours these days. I truly appreciate individuals like you! Take care!!
http://forum.d-dub.com/member.php?121206-PsydayEngendy415
I visit day-to-day a few sites and information sites to read content, but this webpage provides quality based posts.|
https://bookmarkspot.win/story.php?title=samsung-moment-a-phone-that-challenges-the-iphone-4g-3#discuss
You're so interesting! I don't suppose I have read through anything like this before. So great to find another person with some genuine thoughts on this subject. Seriously.. many thanks for starting this up. This site is something that is required on the internet, someone with some originality!|
https://pbase.com/topics/odomismail47/dont_make_these_common_exer
Hello very cool site!! Man .. Excellent .. Amazing .. I will bookmark your blog and take the feeds also? I'm happy to seek out so many useful info here within the post, we want work out extra techniques on this regard, thanks for sharing. . . . . .|
http://www.vitrinreklamekle.xyz/author/hvass26jacobs/
Hi there, I check your blogs daily. Your story-telling style is awesome, keep doing what you're doing!
https://forum.fresh-hotel.org/member.php/47347-hoochupiece243
wow, awesome blog post.
https://www.youtube.com/watch?v=c1ea1eUF3WQ
Remarkable issues here. I'm very glad to peer your article. Thanks so much and I'm looking forward to contact you. Will you please drop me a e-mail?|
https://www.gatesofantares.com/players/pettersonfinnegan9/activity/1568691/
I am regular visitor, how are you everybody? This piece of writing posted at this web site is in fact fastidious.|
http://www.bcsnerie.com/members/barlowweinstein1/activity/1347458/
Great, thanks for sharing this article.Really looking forward to read more. Really Cool.
https://www.youtube.com/watch?v=c1ea1eUF3WQ
Very good article. I absolutely love this website. Continue the good work!|
https://anotepad.com/notes/ih85bgq4
We absolutely love your blog and find nearly all of your post's to be precisely what I'm looking for. Does one offer guest writers to write content for yourself? I wouldn't mind creating a post or elaborating on a lot of the subjects you write in relation to here. Again, awesome website!|
https://jokumseneliasen5.werite.net/post/2022/01/12/3-Methods-To-Get-Endless-Referrals
It's fantastic that you are getting thoughts from this piece of writing as well as from our argument made here.|
https://player.me/manahilahmad/about
Hi there, after reading this remarkable article i am as well cheerful to share my know-how here with mates.|
https://emeraldcube-training.com/forums/users/barreramcmahon8/
Really informative blog post. Cool.
https://www.youtube.com/watch?v=UF8M6Qds_NA
Hey! I'm at work browsing your blog from my new iphone 4! Just wanted to say I love reading your blog and look forward to all your posts! Keep up the outstanding work!|
https://www.stealth-bookmark.win/idm-crack-free-download
Very informative blog.Much thanks again. Really Great.
https://www.youtube.com/watch?v=GSKNrjXsdgk
What's up Dear, are you actually visiting this web site regularly, if so after that you will absolutely take fastidious know-how.|
https://justbookmark.win/story.php?title=link-popularity-how-to-generate-top-grade-links-using-content-aggregators#discuss
Hello everyone, it's my first visit at this web page, and article is
truly fruitful for me, keep up posting such articles or reviews.
Check out my webpage gamefly
Good post. I learn something totally new and challenging on blogs I stumbleupon on a daily basis. It's always useful to read through content from other authors and use something from other sites. |
http://aselah-ejabat.com/index.php?qa=user&qa_1=phelps60drew
Great blog article. Fantastic.
https://rummywealth.app/
Im thankful for the article.Thanks Again. Keep writing.
https://rummygold.app/
When someone writes an article he/she retains the image of a user in his/her brain that howa user can understand it. Therefore that’s why this post is great.Thanks!
https://vasconjardansf.blogspot.com/2022/04/wwwelsotanodelplannercom.html
I am so grateful for your blog article.Thanks Again. Keep writing.
https://luckywinauto.com/สล็อตเว็บตรง-1-บาท
I read this article fully concerning the resemblance of most recent andearlier technologies, it's amazing article.
https://www.openlearning.com/u/lehansson-ra67oh/blog/DetailsYouHaveToBeInformedAboutFunctionalitiesOfCloudPbxSystem
This is very fascinating, You're a very professional blogger. I have joined your feed and sit up for in the hunt for extra of your wonderful post. Also, I've shared your web site in my social networks|
https://www.aeriagames.com/user/q1visdz278/
I'm amazed, I have to admit. Seldom do I come across a blog that's both equally educative and interesting, and without a doubt, you've hit the nail on the head. The problem is something that too few people are speaking intelligently about. I am very happy that I came across this during my hunt for something regarding this.|
https://atavi.com/share/v9v7bwz7awu1
Thanks for the auspicious writeup. It in truth was a entertainment account it. Glance complex to far brought agreeable from you! However, how can we communicate?|
https://telegra.ph/The-Mini-Wonders---Sony-Ericsson-Xperia-X10-Mini-Mobile-Handsets-11-18
Really informative blog article.Thanks Again. Want more.
https://www.youtube.com/watch?v=f9bHt1pcDQY
I couldn't refrain from commenting. Perfectly written!|
http://bezvoprosa.ru/index.php?qa=user&qa_1=mollerupsanders6
certainly like your web site however you need to check the spelling on quite a few of your posts. A number of them are rife with spelling problems and I to find it very troublesome to tell the reality however I will surely come back again.|
http://qooh.me/byrdbirch4
Wow, great article post.Thanks Again. Really Cool.
https://prestigeautodetailingkc.com
Truly when someone doesn't understand then its up to other people that they will assist, so here it takes place.|
http://psnfusion.com/content/index.php?option=com_k2&view=itemlist&task=user&id=1358075
hi!,I like your writing very much! proportion we keep in touch extra about your article on AOL? I require an expert on this area to unravel my problem. May be that’s you! Looking ahead to look you.
https://www.google.lu/url?q=https://www.donbandera.com/fly-banners/
Keep on working, great job!|
http://www.bsaa.edu.ru/bitrix/rk.php?goto=https://licensekeycrack.co/netbalancer-crack-activation-code/