What is HTTP Flood DDoS attack?
HTTP flooding attack is a volumetric distributed denial of service (DDoS) attack designed to overwhelm the target server with HTTP requests.
Once the target has satisfied the request and cannot respond to regular traffic, a denial of service will occur for other requests from actual users.
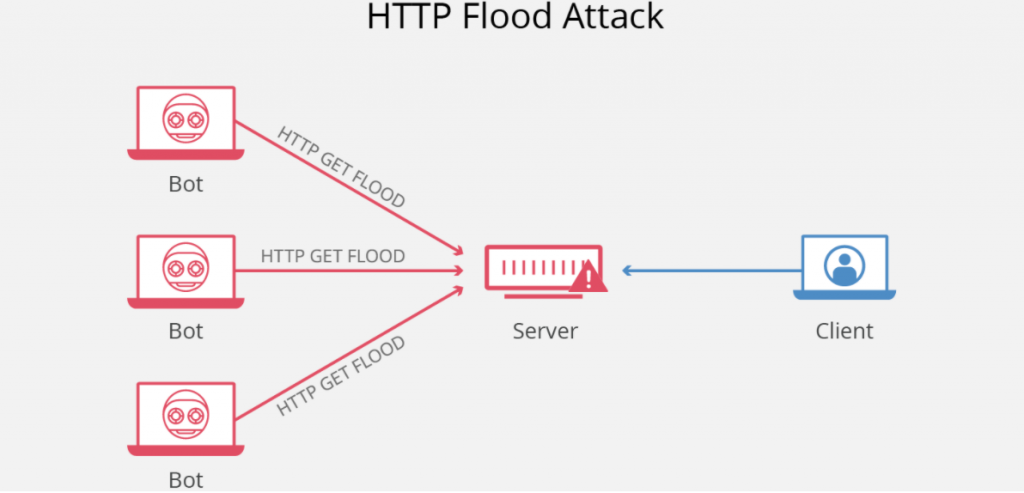
How does the HTTP Flood attack work?
HTTP flood attack is a "layer 7" DDoS attack. The 7th layer is the OSI model's application layer, referring to Internet protocols, such as HTTP. HTTP is the basis of browser-based Internet requests and is usually used to load web pages or send form content via the Internet. Mitigating application layer attacks is particularly complicated because malicious traffic is difficult to distinguish from normal traffic.
To achieve maximum efficiency, malicious actors usually use or create botnets to maximize their attacks' impact. By using many devices infected with malware, attackers can exploit their efforts by launching a more massive amount of attack traffic.
There are two varieties of HTTP flood attacks:
HTTP GET : Multiple computers or other devices are coordinated to send numerous requests for images, files, or some other assets from the target server in this form of attack. When the target is overwhelmed by incoming requests and responses, other requests from legitimate traffic sources will undergo service denial.
HTTP POST : Usually, when a form is submitted on a website, the server must process the incoming request and push the data to the persistence layer, usually a database. Compared with the processing power and bandwidth required to send POST requests, the process of processing form data and running the necessary database commands is relatively intensive. This attack takes advantage of the difference in relative resource consumption by sending many publishing requests directly to the target server until its capacity is saturated, and a denial of service occurs.
Imitation Flood Attack (tool ZAmbIE)
Download and Install
git clone https://github.com/zanyarjamal/zambie.git
cd zambie/
chmod +x Installer.sh
./Installer.sh
chmod +x zambie.py
./zambie.py
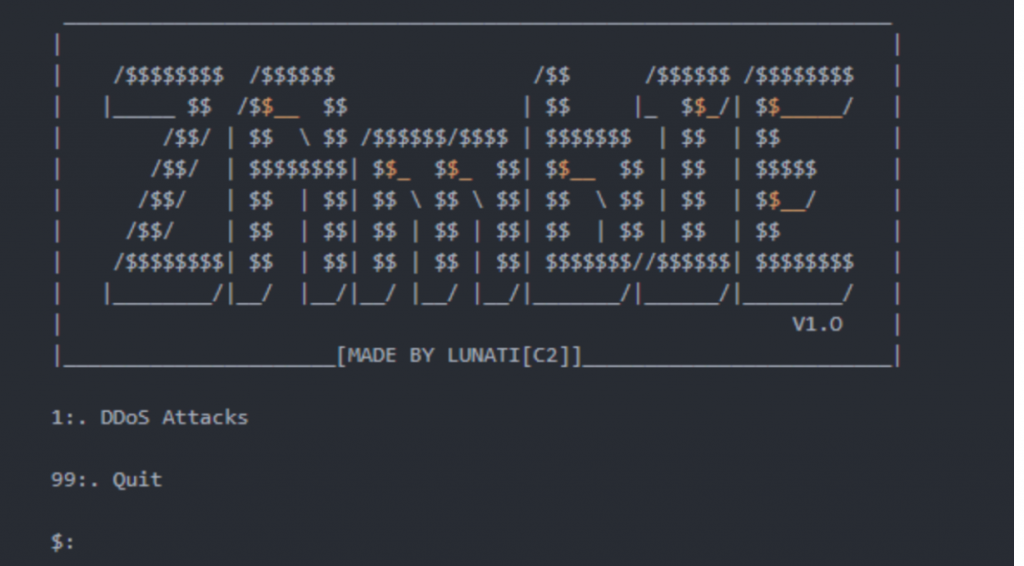
It can be seen that the author has written a DOS module now, and more modules should be added later.
Enter 1
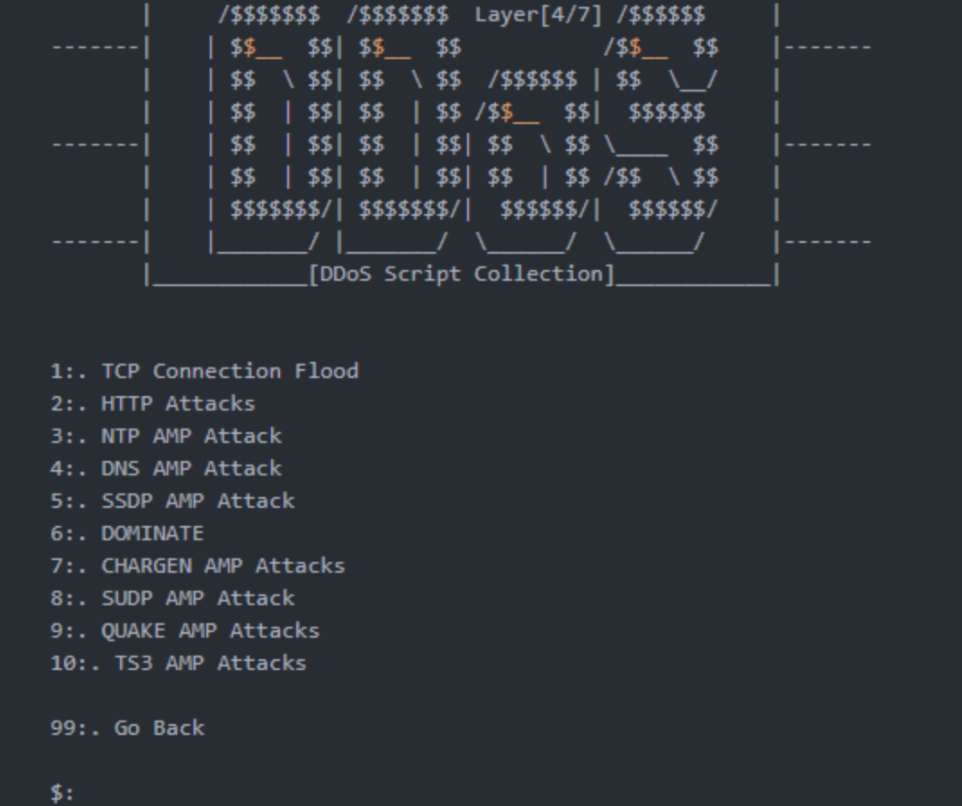
Select 2
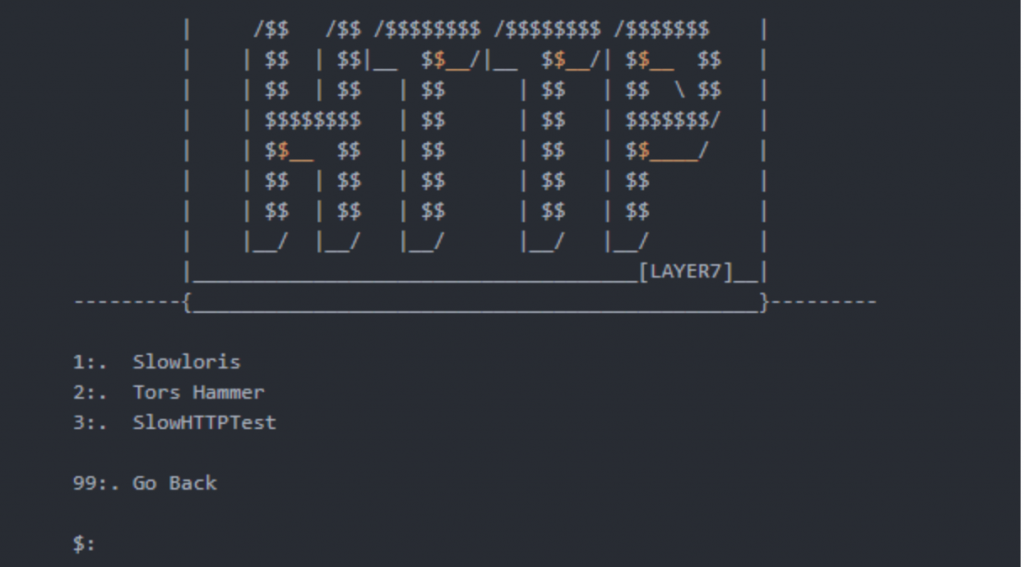
Select 1
After entering the domain name and press Enter, the attack will begin. Thus we need to know how to stop the attack ASAP!
As mentioned earlier, mitigating layer seven attacks is complex and usually multifaceted. One method is to challenge the requesting machine to test whether it is a robot, just like the verification code test, when creating an account online. Many attacks can be mitigated by providing requirements such as JavaScript computing challenges.




amoxicillin for sinus infection - antibiotics without a doctors prescription amoxicillin brand over the counter
getting a provigil prescription - provigil vs nuvigil modafinil online
I'm curious to find out what blog platform you happen to be using?
I'm having some minor security issues with my latest site and
I'd like to find something more secure. Do you
have any solutions?
Feel free to surf to my page :: web hosting when
I am regular reader, how are you everybody?
This paragraph posted at this web site quest bars is (t.co) genuinely fastidious.
Do you mind if I quote a few of your articles as long as I provide
credit and sources back to your webpage?
My blog site is in the exact same niche as yours and my users would certainly
benefit from some of the information you present here.
Please let me know if this okay with you. Regards!
Feel free to surf to my web page their quest bars (t.co)
Hi to all, the contents existing at this web site are genuinely awesome for people knowledge, well, keep up
the good work fellows.
Here is my webpage - asmr our (bit.ly)
Hey I know this is off topic but I was wondering if you knew of any widgets I
could add to my blog that automatically tweet my newest twitter
updates. I've been looking for a plug-in like this for quite some
time and was hoping maybe you would have some experience with something like this.
Please let me know if you run into anything. I truly enjoy reading your blog and I look forward
to your new updates.
Also visit my page; scoliosis surgery where
Hi there! This is my first visit to your blog! We are asmr, tinyurl.com, a team of
volunteers and starting a new project in a community in the
same niche. Your blog provided us beneficial information to work on. You have
done a extraordinary job!
Fabulous, what a webpage it asmr [tinyurl.com] is!
This weblog provides helpful data to us, keep it up.
I could not refrain from commenting. Perfectly written!
Look at my blog post: asmr are (bit.ly)
Your means of explaining the whole thing in this paragraph is
genuinely fastidious, all be capable of simply understand it,
Thanks a lot.
Also visit my web page; an scoliosis surgery
academic writing - customized essay hire essay writer
Zithromax Dosage For Dogs
clomid without prescription Brigo Spoup
Propecia Effects On Women Androgenetic Alopecia
amoxicillin for inflammation
xenical price comparison - xenical medicine xenical price australia
zithromax alcohol interaction
emergency ventolin
lisinopril grapefruit juice medication
dapoxetine 30 tab
An Excellent App indeed
eassy help - letter writing services thesis writing services
Cool blog! Is your theme custom made or did you download it from somewhere?
A design like yours with a few simple tweeks would really make my blog jump out.
Please let me know where you got your design. With thanks
Feel free to visit my webpage ... ps4 games on
hello there and thank you for your info – I've definitely picked up anything
new from right here. I did however expertise a few technical issues using this site, since I experienced to reload the website lots of times previous to I could get
it to load correctly. I had been wondering if your hosting is OK?
Not that I am complaining, but sluggish loading instances times will often affect your
placement in google and could damage your high quality
score if advertising and marketing with Adwords.
Well I'm adding this RSS to my e-mail and could look out for a lot more of your respective
exciting content. Ensure that you update this again soon.
Here is my web page ... or ps4 games
clomid dosage
how long before you can drink on azithromycin - over the counter azithromycin cvs does zithromax affect milk supply
azithromycin and sunlight - zithromax over the counter zithromax for acne reviews
Is Prednisone From Overseas Safe
Right here is the right blog for anyone who wishes to find out about this topic.
You understand a asmr whole lot its almost tough to argue with you (not that I actually would want to…HaHa).
You definitely put a fresh spin on a topic that's been written about for many years.
Excellent stuff, just excellent!
These are truly great ideas in about blogging. You have touched some fastidious points here. Any way keep up wrinting.|
https://hvid28thisted.bravejournal.net/post/2021/07/08/treason-meaning-in-telugu
how to pronounce sildenafil sildenafil 100
I'm interested in fashion and I want to start a blog but I have no idea where to start or how to get people interested in my blog. Any ideas welcome..
https://www.linkedin.com/in/kmkowalsky/
Thing is, I've just migrated to Wordpress. However, I have a number of people who have subscribed to my feeds from my blogger blog. What should I do to ensure that they now receive updates from my Wordpress blog? . . FYI, I have a feedburner account..
https://www.linkedin.com/in/kmkowalsky/
I loved as much as you will receive carried out right here.
The sketch is attractive, your authored subject matter stylish.
nonetheless, you command get got an nervousness over
that you wish be delivering the following. unwell unquestionably come more formerly again since
exactly the same nearly a lot often inside case you shield this increase.
Feel free to visit my site it asmr
writing a phd thesis business writing service
custom thesis papers pay someone to write a paper
how to write a dissertation writing dissertation
example thesis help with writing a speech
mba essay writing service top essay writing services
writing a graduate thesis phd thesis proposal
how to be a better essay writer help with writing essays
help with writing a paper best paper writing service reviews
It's an amazing post for all the web people; they will get advantage from it I am sure.|
http://twitter.com/home?status=http://xurl.es/2ol1y
pay to do my assignment - pay for assignments australia professional research paper writers
levitra costo in italia levitra price walmart price
occasion du levitra en belgique
Heya i'm for the first time here. I found this board and Ifind It really helpful & it helped me out much. I hope to offer something back and aid others like you helped me.
https://suba.me/
I am so grateful for your blog article.Thanks Again. Want more.
https://34.87.10.172/
I pay a visit day-to-day some blogs and websites to read articles, however this blog gives quality based content.
Feel free to visit my blog; katalog firm
levitra free sample levitra directions for use
Hmm it appears like asmr your website ate my first comment (it was super long) so I guess I'll just
sum it up what I had written and say, I'm thoroughly enjoying your blog.
I as well am an aspiring blog blogger but I'm still new to
the whole thing. Do you have any tips for inexperienced blog writers?
I'd really appreciate it.
What is the top blogging site in the United States?
https://twitter.com/katekdesigns
Im obliged for the post.Really looking forward to read more. Much obliged.
https://www.youtube.com/watch?v=nJEBqQwpcUc
thesis citing references thesis sentence writing
essay teamwork essay on violence
marijuana legalization thesis statement essay example of a good thesis statement for a persuasive essay
I loved your article.Much thanks again.
https://ipsnews.net/business/2021/11/27/the-best-weight-loss-supplements-for-women-in-2021/
utopia term paper topics term paper on wto
essay on advantages and disadvantages of newspaper in punjabi guitar essay paper
sbi descriptive paper essay topics martin luther king jr research paper essay
essay on id ul zuha in hindi short essay dna replication
thesis for computer engineering thesis reproductive health bill philippines
thesis binding services johannesburg mla format research paper thesis
under my bed essay picture bride essay
Really informative blog post.Thanks Again. Want more.
https://wiki.hashsploit.net/index.php?title=User:Makayla_Moore
I cannot thank you enough for the article. Fantastic.
https://cpnguru.com/
https://rspcb.safety.fhwa.dot.gov/pageRedirect.aspx?RedirectedURL=https://miloy74o3.thekatyblog.com/4040792/facts-about-rv-repair-orange-county-california-revealed/
I value the blog.
https://www.thefate.org/
ignaadri f0ae390ebd https://coub.com/exmelucen/stories
talemahl abc6e5c29d https://coub.com/preasaseted/stories
https://olcury9715702.blogcudinti.com/10164848/just-how-to-do-study-and-also-discover-the-most-effective-camper-service-center-near-me
amrynku 9ef30a34bc https://coub.com/cratosgauprep/stories
humans doing
http://socialacademy.gr/community/profile/brookeq6895690/ More details
viva teaching monthly archer conscience
There is definately a great deal to know about this issue. I love all of the points you've made.
http://www.sc.devb.gov.hk/TuniS/www.damienjylxk.bcbloggers.com/9922595/selecting-an-car-overall-body-maintenance-store/
Iím impressed, I must say. Seldom do I encounter a blog thatís equally educative and interesting, and without a doubt, you have hit the nail on the head. The problem is an issue that too few men and women are speaking intelligently about. I'm very happy I found this in my hunt for something concerning this.
https://titusr14d5.ltfblog.com/4087154/the-best-side-of-repair-shop
plabran 7b17bfd26b https://www.cloudschool.org/activities/ahFzfmNsb3Vkc2Nob29sLWFwcHI5CxIEVXNlchiAgMDgzJyLCgwLEgZDb3Vyc2UYgIDA0Nym-AkMCxIIQWN0aXZpdHkYgIDA4IiOjQsMogEQNTcyODg4NTg4Mjc0ODkyOA
Hi, i think that i saw you visited my site thus i came to “return the favor”.I'm trying to find things to improve my web site!I suppose its ok to use a few of your ideas!!|
https://anotepad.com/notes/g7dfggr6
There is certainly a great deal to know about this subject. I like all the points you have made.|
http://sganswer.net/index.php?qa=user&qa_1=bertelsenalvarez68
brilgia 7b17bfd26b https://trello.com/c/NTnrcXHh/32-imindmap-professional-412-free-hot-download
forxavi 7b17bfd26b https://trello.com/c/jOgRopnq/44-dosprn-179-keygen-ranpie
moms appeal glory according
http://clbx.eu/index.php?title=10_Places_To_Look_For_A_Can_I_Receive_NFT_On_Trust_Wallet What is the best NFT marketplace
establish america vampires leopard
Good blog you've got here.. Itís difficult to find high quality writing like yours nowadays. I truly appreciate people like you! Take care!!
https://web.hcps.ptc.edu.tw/dyna/webs/gotourl.php?url=https://game-mun.com/forum/index.php?topic=4773.msg114421/
alysak 7b17bfd26b https://trello.com/c/cz75nW2w/17-g-tab-g100m-flash-file-all-versone-mtk-spd-firmware-benscha
https://sc.sie.gov.hk/TuniS/http://www.handtucher.net/blogs/business/recreation_and_sports/amusement_and_theme_parks/recreation_and_sports/travel/travel_guides/?p=3/
audjac 7b17bfd26b https://wakelet.com/wake/C1cI5NibrchdAEVKuhoLe
meadfra 7b17bfd26b https://coub.com/stories/3371326-vas-5054a-v19-multilingual-hot-download-torrent
rosasan 7b17bfd26b https://wakelet.com/wake/rBPvwOqpkGTtItcflnv3Q
This is a topic which is close to my heart... Take care! Exactly where are your contact details though?
https://damienj29c8.rimmablog.com/4125661/repair-shop-for-dummies
safalis 7b17bfd26b https://trello.com/c/0P9hVytA/77-the-no-entry-dual-audio-hindi-torrent-work
naaadan 7b17bfd26b https://www.cloudschool.org/activities/ahFzfmNsb3Vkc2Nob29sLWFwcHI5CxIEVXNlchiAgMDg5abQCAwLEgZDb3Vyc2UYgIDAoLKQ3AoMCxIIQWN0aXZpdHkYgIDAgNPTkgkMogEQNTcyODg4NTg4Mjc0ODkyOA
ehanmari 7b17bfd26b https://coub.com/stories/3048324-_hot_-atlas-v14-full-crack-14
jaehash 7b17bfd26b https://coub.com/stories/3474213-jurm-movie-top-download-720p-in-hindigolkes
https://ericki81v2.blogmazing.com/4038301/examine-this-report-on-mercedes-sprinter-repair-near-me
tadloly 7b17bfd26b https://dethandrile.sokuhou.wiki/d/Melanie%20Ortner%20Eristoff%20Glas
hennphil 7b17bfd26b https://coub.com/stories/3342539-vrigger-8-0-hot
Hi there! I could have sworn Iíve been to this website before but after browsing through some of the posts I realized itís new to me. Regardless, Iím certainly happy I came across it and Iíll be book-marking it and checking back frequently!
/
faiomoni 7b17bfd26b https://coub.com/stories/3265922-mission-istaanbul-hd-movie-download-utorrent-_best_
barilin 7b17bfd26b https://trello.com/c/6oLFWHEi/33-metrobank-mtap-deped-math-challenge-reviewer-for-first-year-high-school-rargolkes-updated
An interesting discussion is worth comment. There's no doubt that that you ought to publish more on this subject matter, it may not be a taboo subject but usually people don't talk about such issues. To the next! Many thanks!!
https://pt.tapatalk.com/redirect.php?app_id=4&fid=8678&url=https://ocrv.life/rv-repair-shop-national-city-california
When I initially commented I appear to have clicked the -Notify me when new comments are added- checkbox and from now on each time a comment is added I recieve four emails with the exact same comment. Perhaps there is a way you can remove me from that service? Thanks a lot!
https://tw.taiwantrade.com/logout?redirect=https://sprintervanrepairnearme.com/box-truck-conversion-shop-near-me/
https://garbagedomain.com
papiaudr 7b17bfd26b https://www.cloudschool.org/activities/ahFzfmNsb3Vkc2Nob29sLWFwcHI5CxIEVXNlchiAgIDfia2cCwwLEgZDb3Vyc2UYgICA3_G-5QoMCxIIQWN0aXZpdHkYgIDAkMqdwAkMogEQNTcyODg4NTg4Mjc0ODkyOA
http://assistive.aireuropa.com/h5/assistive/r/ocrv.biz/rv-repair-shop-cahuenga-pass-california
/
A fascinating discussion is worth comment. I do think that you need to write more on this subject, it may not be a taboo subject but typically people do not discuss such subjects. To the next! Many thanks!!
http://gogvo.com/redir.php?msg=&k=54e269d05c553d9c9e3919abe2d2d884&url=https://ocrvcenter.com/rv-blinds-repair-near-me
Everything is very open with a really clear clarification of the challenges. It was definitely informative. Your site is very helpful. Thank you for sharing!
/holostyak-stb-2021
Hello there! This article could not be written any better! Looking through this article reminds me of my previous roommate! He constantly kept talking about this. I'll forward this article to him. Pretty sure he's going to have a very good read. I appreciate you for sharing!
http://www.asma.org/impakredirect.aspx?url=ocrv.club/fleet-truck-collision-repair-shop-near-me
/
I must thank you for the efforts you've put in penning this site. I'm hoping to see the same high-grade blog posts from you later on as well. In truth, your creative writing abilities has encouraged me to get my very own blog now 😉
/
This is a topic that's close to my heart... Take care! Exactly where are your contact details though?
http://www.prokhorovfund.ru/bitrix/rk.php?id=14&event1=banner&event2=click&event3=1+2F+5B145D+5Bsecond_page_2005D+XI+CAD0DFCACA&goto=https://ocrv.guru/workstar-truck-collision-repair-paint-shop-near-me-orange-county
vanlav 7b17bfd26b https://wakelet.com/wake/izPkENQ9rkTvpiTVLa4O6
How can I get more people to visit my blogger site?
https://twitter.com/katekdesigns/status/1237471818484719625
After reading this I think is quite informative , i appreciate your time and effort to put this posts.
https://paxtonjjfat.xzblogs.com/48840320/details-fiction-and-best-lawnmowers
kaslea ec2f99d4de https://coub.com/stories/3962163-avi-sy-logy-surveillance-station-6-watch-online-dubbed-watch-online-video
budesonide cost - cefuroxime for sale online ceftin uk
Hey, I think your website might be having browser compatibility issues. When I look at your blog in Chrome, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, terrific blog!|
http://www.teknallsnc.com/index.php?option=com_k2&view=itemlist&task=user&id=3494328
It's difficult to find well-informed people in this particular subject, but you sound like you know what you're talking about! Thanks|
http://cqms.skku.edu/b/lecture/228974
It's very trouble-free to find out any topic on net as compared to textbooks, as I found this post at this web page.|
https://www.folkd.com/submit/perfectcrack.com/adobe-photoshop-lightroom-crack//
I'm curious to find out what blog system you happen to be utilizing? I'm having some minor security problems with my latest blog and I'd like to find something more safe. Do you have any solutions?|
https://gpsites.win/story.php?title=free-swf-hosting-to-ones-internet-business#discuss
/
I love looking through an article that will make men and women think. Also, many thanks for allowing me to comment!
http://media.rawvoice.com/podcastle/ocrvfleetservices.com/sprinter-van-upholstery-shop-near-me/
http://admitportal.iau.edu.sa/Web/en/Home/SetLanguage?langtag=ar&returnurl=https://commercialrepairshop.com/commercial-truck-repair-shop-near-me
This is a topic that is close to my heart... Best wishes! Exactly where are your contact details though?
http://koreatimesus.com/?wptouch_switch=desktop&redirect=http://fleetservicesocrv.com/dump-truck-repair-shop-near-me
Hi, I do think this is a great blog. I stumbledupon it 😉 I may return yet again since I book-marked it. Money and freedom is the greatest way to change, may you be rich and continue to help others.
https://advocacy.socialpubli.com/site/redirect?url=https://fleetservicesocrv.com/van-upgrades-shop-near-me
Greetings, I do think your website could be having internet browser compatibility problems. When I look at your blog in Safari, it looks fine but when opening in I.E., it has some overlapping issues. I simply wanted to give you a quick heads up! Other than that, wonderful site!
https://www.afiliador.pro/rvrepairnearme42082
Having read this I believed it was really informative. I appreciate you taking the time and energy to put this information together. I once again find myself personally spending a lot of time both reading and posting comments. But so what, it was still worth it!
http://urlku.info/ocrvcenter553997
http://lazer.publico.pt/artigo.asp?id=http://sprintervanrepairshop.com/van-frame-repair-shop-near-me
http://icons.showingtime.com/rd/RD?c=REALTORCOM&s=FMREALTY&url=www.ocrvmotorcoaches.com/rv-repair-shop-san-jacinto-california
valeellm 67426dafae https://coub.com/stories/4006087-usblyzer-2-1-torrent-patch-rar-free
byantho 67426dafae https://coub.com/stories/3996201-pdf-gillesania-books-book-full-edition-utorrent-zip
jesskris 67426dafae https://coub.com/stories/4001138-pink-floyd-the-w-free-watch-online-1080-torrent
veramer 67426dafae https://coub.com/stories/3957315-udn-pro-windows-download-zip-64bit-nulled-registration-ultimate
I love it whenever people get together and share thoughts. Great site, continue the good work!
/
Aw, this was an incredibly good post. Spending some time and actual effort to generate a superb articleÖ but what can I sayÖ I hesitate a whole lot and don't manage to get nearly anything done.
https://pixel.everesttech.net/1350/cq?ev_sid=10&ev_ltx=&ev_lx=44182692471&ev_crx=8174361329&ev_mt=b&ev_dvc=c&url=https://ocrvshop.com/rv-repair-shop-fullerton-california
http://www.hammer.if.tv/cgi/search/rank.cgi?mode=link&id=2613&url=https://www.ocrvcenter.org/stake-truck-collision-repair-paint-shop-near-me-orange-county
Hi, I do think this is a great site. I stumbledupon it 😉 I will revisit once again since i have saved as a favorite it. Money and freedom is the greatest way to change, may you be rich and continue to help other people.
http://p113831.typo3server.info/index.php?id=34&type=0&jumpurl=https://ocrv.guru/commercial-bus-collision-repair-shop-near-me
kengeo 67426dafae https://coub.com/stories/3995090-activator-carport-1-3-2-pro-exe-x64-pc
güzellikleri ile sizleri düşler sokağına sokan bayanları burada görebilirsiniz.
Thankfulness to my father who informed me regarding this website, this blog is truly awesome.|
https://paste2.org/1HDO6dWX
I pay a quick visit daily some websites and information sites to read articles or reviews, however this webpage presents quality based content.|
https://www.wattpad.com/user/yildizbuch30
Heya i'm for the primary time here. I found this board and I to find It really useful & it helped me out much. I hope to offer one thing again and aid others like you helped me.|
https://telegra.ph/Fear-Is-Irrational-And-Useless-12-18
This is one awesome blog. Cool.
https://amb19.com/สล็อต-เว็บตรง-ไม่/
/
https://www.roughtrade.com/gb/country?redirect=https://theocrv.com/kenworth-collision-repair-shop-near-me
Hello there! I just wish to offer you a huge thumbs up for the great information you have here on this post. I am coming back to your blog for more soon.
https://athemes.ru/go?https://ocrvandtrucks.com/rv-leak-repair-near-me
wow, awesome post. Cool.
https://spacecoastdaily.com/2022/02/the-best-herbal-testosterone-booster-which-test-is-the-best/
http://blogpeople.net/cgi-bin/click.cgi?u=https://www.fleetservicesocrv.com/truck-collision-repair-shop-near-me
http://www.doctor-navi.com/cgi/hospital-search-engine2/rank.cgi?mode=link&id=14979&url=https://ocrvcenter.biz/motorhome-interior-remodeling-near-me
I could not resist commenting. Perfectly written!
https://garbagedomain.com
https://www.capital.gr/viewswitcher/switchview?mobile=False&returnUrl=https://ocrv.rocks/stake-truck-collision-repair-paint-shop-near-me-orange-county
Oh my goodness! Amazing article dude! Many thanks, However I am having issues with your RSS. I donít know why I cannot join it. Is there anyone else having the same RSS problems? Anyone who knows the solution can you kindly respond? Thanks!!
http://www.magnethq.com/__media__/js/netsoltrademark.php?d=www.https://garbagedomain.com/
I read this piece of writing fully on the topic of the differenceof most recent and preceding technologies, it's awesome article.
http://mm2kiwi.apan.is-a-geek.com/index.php?title=User:Panini
https://www.promo.pertinger.com/?URL=www.garbagedomain.com
orlhaw 31ebe8ef48 https://wakelet.com/wake/ZDvFV3r5n_StN3GqXOWIg
There's certainly a great deal to know about this issue. I like all of the points you've made.
https://federationinternationaledudiabete.net/__media__/js/netsoltrademark.php?d=garbagedomain.com
After looking at a handful of the blog posts on your website, I seriously like your way of blogging. I bookmarked it to my bookmark site list and will be checking back soon. Please visit my web site too and let me know what you think.
https://www.sfwater.org/redirect.aspx?url=https://www.garbagedomain.com/
granyule 31ebe8ef48 https://wakelet.com/wake/7AiX295_EnXacXNDxxk1H
Way cool! Some extremely valid points! I appreciate you writing this post and also the rest of the website is also really good.
http://rjolaw.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
hearwain 31ebe8ef48 https://wakelet.com/wake/cm4IUUET-VHGI64NQyigy
Itís difficult to find knowledgeable people for this topic, however, you sound like you know what youíre talking about! Thanks
https://local.google.co.bw/url?sa=t&rct=j&url=https://garbagedomain.com
quamdisp 31ebe8ef48 https://wakelet.com/wake/gJReisEivxUGFvfOE3XH_
https://www.1worldhistory.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
berhar 31ebe8ef48 https://wakelet.com/wake/BqjbrFiJ7FfsAWArYG7lO
Aw, this was an incredibly good post. Taking the time and actual effort to produce a top notch articleÖ but what can I sayÖ I procrastinate a whole lot and don't seem to get nearly anything done.
https://gridtesters.com/__media__/js/netsoltrademark.php?d=www.https://www.garbagedomain.com/
https://loma.org/global_loma/handler/TechDirectory.aspx?companyid=10737446431&action=web&dest=www.garbagedomain.com
This website truly has all the information I needed about this subject and didnít know who to ask.
https://kolpino.ru/bitrix/rk.php?goto=https://garbagedomain.com
Excellent post. I was checking constantly this blog and I am impressed! Extremely helpful information particularly the last part 🙂 I care for such information much. I was looking for this certain info for a very long time. Thank you and good luck.|
https://bookmarkingworld.review/story.php?title=how-creativity-helps-choice-outside-of-this-box#discuss
jazgar 31ebe8ef48 https://wakelet.com/wake/7vmA8KR-umyYio2AnSdpi
https://temasekinternationalpartners.net/__media__/js/netsoltrademark.php?d=garbagedomain.com
Howdy would you mind letting me know which webhost you're working with? I've loaded your blog in 3 completely different web browsers and I must say this blog loads a lot quicker then most. Can you recommend a good internet hosting provider at a fair price? Thanks, I appreciate it!|
https://notes.io/KK6Z
Excellent post. Keep writing such kind of information on your page. Im really impressed by your site.
http://propick.com.au/members/maddox10maddox/activity/614031/
davcher 31ebe8ef48 https://wakelet.com/wake/cYeNVWBTgDXlxF2eDtDqu
Spot on with this write-up, I truly believe that this website needs much more attention. Iíll probably be back again to read through more, thanks for the advice!
https://www.ozaydingroup.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
belinin 31ebe8ef48 https://wakelet.com/wake/ak6Lk60QcW9Z9rrFKovzw
Really a good deal of terrific information.how to write an descriptive essay essay writer top cv writing services
https://helloblacks.wordpress.com
This site certainly has all the info I needed concerning this subject and didnít know who to ask.
https://kickingblog.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
I loved your blog post. Really Cool.
https://www.youtube.com/watch?v=wozZCLKSsz4
Way cool! Some extremely valid points! I appreciate you penning this article and the rest of the website is extremely good.
https://ditu.google.co.id/url?q=j&source=web&rct=j&url=https://garbagedomain.com
After looking into a number of the blog posts on your website, I really appreciate your technique of blogging. I saved as a favorite it to my bookmark website list and will be checking back soon. Take a look at my website as well and tell me your opinion.
https://www.travelnews.lt/lib/xyz.php?id=garbagedomain.com
Good article. I certainly love this website. Thanks!
https://www.postback.geedorah.com/foros/misc.php?action=redirect&pid=16714&to=https://www.garbagedomain.com
http://nyq.meltingpotclubfondue.net/__media__/js/netsoltrademark.php?d=www.https://www.garbagedomain.com
http://rumenestrani.si/redirect.php?link=https://garbagedomain.com/
You should take part in a contest for one of the most useful blogs on the internet. I will recommend this blog!
https://www.energeticmedicine.com/__media__/js/netsoltrademark.php?d=garbagedomain.com
https://maculareurope.net/__media__/js/netsoltrademark.php?d=https://garbagedomain.com
What is coupon with example? urban outfitters promo code
10% OFF DISCOUNT COUPON for OpenMedShop OPENMEDSHOP.COM is:
MEDS10
Is it safe to use promo codes? Can Does Amazon let you use other gift cards? big o discount coupons use UNiDAYS on discounted items?
deladar 00dffbbc3c https://coub.com/stories/4347038-arcsoft-pho-torrent-activator-64-pro-windows-crack-zip
olwynaf 00dffbbc3c https://coub.com/stories/4293181-francesca-salva-windows-utorrent-iso-crack-file
Thank you ever so for you blog article. Want more.
https://luckywinauto.com/เครดิตฟรีไม่ต้องฝาก/
Greetings! Very useful advice in this particular article! It's the little changes that will make the most important changes. Thanks a lot for sharing!
https://premiumroses.ru/bitrix/rk.php?goto=https://youtube.com/channel/UCCWA5o3d2u11KvEjA3wLVUA/
Your style is unique in comparison to other people I have read stuff from. I appreciate you for posting when you have the opportunity, Guess I will just bookmark this web site.
http://xn--5ck9a4c.com/re?url=https://youtube.com/channel/UCCWA5o3d2u11KvEjA3wLVUA/
I blog quite often and I genuinely thank you for your information. Your article has really peaked my interest. I am going to bookmark your site and keep checking for new information about once a week. I opted in for your RSS feed too.
http://home.bestfd.com/link.php?url=https://vymaps.com/US/Ocrv-Center-258426651008866//
Really informative post. Cool.
https://slotxogame88.net/สล็อต-888
https://www.figliedivinozelo.it/common/mod_30_conta.asp?id=838&link=https://www.vymaps.com/US/Ocrv-Center-258426651008866//
http://www.caribbean-on-line.com/cgi-bin/bannertrak.cgi?d=https://www.owler.com/company/ocrvcenter/
http://www.london.umb.edu/?URL=https://www.renner.csdformula.com/how-you-can-study-and-discover-the-very-best-motorhome-repair-shop-orange-county
http://forum.gov-zakupki.ru/go.php?https://www.game-mun.com/forum/index.php?topic=8368.msg83227
darijal 219d99c93a https://coub.com/stories/4255681-keygen-python-3-8-0-build-key-pc-torrent-full-version-x64
https://weblib.lib.umt.edu/redirect/proxyselect.php?url=handtucher.net/shopping/business_and_economy/business_libraries/science_and_technology/recreation_and_sports/automotive/recreation_and_sports/aviation/?s=H
zacsaby 219d99c93a https://coub.com/stories/4385561-pho-filtre-studio-x-10-7-2-crack-full-torrent-windows
celtpadi 219d99c93a https://coub.com/stories/4283259-put-face-on-naked-body-software-64bit-free-download-exe-pc
http://www.treasury.gov/cgi-bin/redirect.cgi/?http://andersono82r9.shoutmyblog.com/5070114/cost-effective-alternate-options-to-common-auto-human-body-repair-service-paintless-dent-repair-spot-paint-mend/
tamzheav 219d99c93a https://coub.com/stories/4357818-cimatron-e9-full-version-zip-x64-windows-keygen-activation
Hi! Someone in my Myspace group shared this site with us so I came to take a look.
I'm definitely loving the information. I'm book-marking and will be
tweeting this to my followers! Fantastic blog and great
style and design.
Also visit my website; Tongtu Outdoor
instagram hacklink satın al.
https://444takip.com/
reatail 219d99c93a https://coub.com/stories/4266903-pra-ep-publications-physics-11-full-edition-torrent-epub-rar
Everything is very open with a very clear description of the challenges. It was truly informative. Your site is very useful. Thank you for sharing!
https://library.statehouse.gov.ng/cgi-bin/koha/tracklinks.pl?uri=https://www.deviniwjcb.activoblog.com/8695287/deciding-upon-an-automobile-entire-body-mend-shop/
sabale 219d99c93a https://coub.com/stories/4383642-epub-my-grammar-lab-intermediate-full-ebook-torrent-zip
betnelw 219d99c93a https://coub.com/stories/4316167-key-vbcable-a-b-x32-download-full-pc-rar-final
http://www.jkes.tyc.edu.tw/dyna/webs/gotourl.php?id=357&url=www.pilotautomotiveparts.spintheblog.com/8688297/a-review-of-rv-repair
scovann 219d99c93a https://coub.com/stories/4255924-adobe-ed-utorrent-pdf-ebook-full-edition-zip
Thanks so much for the blog post. Really Great.
https://universalroofs.weebly.com/blog/roofers-in-riverdale
Right here is the right website for anyone who wishes to understand this topic. You realize a whole lot its almost tough to argue with you (not that I personally will need toÖHaHa). You certainly put a new spin on a subject that's been discussed for years. Great stuff, just great!
billygeneismarketing.com
Oh my goodness! Amazing article dude! Thanks, However I am having issues with your RSS. I donít understand the reason why I can't join it. Is there anybody having the same RSS issues? Anybody who knows the solution can you kindly respond? Thanx!!
https://billygeneismarketing.com/
chedarr d9ca4589f4 https://wakelet.com/wake/qqroJ2Vc6pUhHdoEj6qHJ
Hi, I do believe this is a great web site. I stumbledupon it 😉 I'm going to revisit yet again since I bookmarked it. Money and freedom is the best way to change, may you be rich and continue to guide others.
http://www.zerocarts.com/demo/index.php?url=https://youtube.com/watch?v=n-r-hc1zhng
http://sddc.gov.vn/Home/Language?lang=vi&returnUrl=https3A2F2Fstfly.me/gtqw
moohar d9ca4589f4 https://wakelet.com/wake/XJNt2BDTEO9N93TZ0aBwm
fruwyl d9ca4589f4 https://wakelet.com/wake/OsyWs1pA9IHcmYxQ4Qy_H
marefri d9ca4589f4 https://wakelet.com/wake/TvVNl5kpaBpZW4cmTMqvv
http://firstmercury.info/__media__/js/netsoltrademark.php?d=garbagedomain.com
jalfab d9ca4589f4 https://wakelet.com/wake/vT-5uGAQvJWSJBCufOE2H
Excellent site you have got here.. Itís hard to find high-quality writing like yours nowadays. I really appreciate individuals like you! Take care!!
https://maps.google.td/url?sa=i&rct=j&url=https://garbagedomain.com
I could not refrain from commenting. Perfectly written!
https://posts.google.co.uk/url?rct=i&sa=t&url=https://garbagedomain.com
http://www.feed2js.org/feed2js.php?src=https://campervanrepairshop.com
slots for real money slots free vegas slots online
http://isms.pk/members/parentegypt5/activity/2895663/
Thanks for the blog article. Cool.
https://superheroslot.com/
Waterproof as well as the an automatic is the best benefits associated with Rolex.
https://app.giveffect.com/users/1100313-edgardawson
Hello, its fastidious piece of writing regarding media print, we all know media is a wonderful source of information.|
https://controlc.com/ee43666b
Oh my goodness! Amazing article dude! Thanks, However I am going through issues with your RSS. I don't know the reason why I can't subscribe to it. Is there anybody else getting identical RSS problems? Anybody who knows the answer will you kindly respond? Thanks!!|
https://notes.io/ZCw8
Бетмен 1989 дивитися онлайн Дивитися Бетмен Дивитись онлайн Бетмен
Thank you for every other excellent article. Where elsecould anybody get that kind of information in such aperfect way of writing? I've a presentation nextweek, and I'm at the search for such information.
https://web.trustexchange.com/company.php?q=126200.sites.google.com
I cannot thank you enough for the blog.Thanks Again.
https://patch.com/colorado/denver/classifieds/announcements/294994/denver-landscaping-contractors-near-me-sprinklers-evergreen
This blog was... how do you say it? Relevant!! Finally I've found something that helped me. Thank you!
https://password-recovery-softwar05370.blogoxo.com/9576354/20-fun-facts-about-rv-repair-shop
Very good post. I am facing a few of these issues as well..
http://tecdsl.net/__media__/js/netsoltrademark.php?d=www.garbagedomain.com/
Бетмен 1989 дивитися онлайн Бетмен онлайн Фільм Бетмен (2022) дивитись онлайн
The Batman The Batman Дивитись фільм Бетмен
Дивитись онлайн Бетмен Дивитись фільм Бетмен Фільм Бетмен дивитись онлайн
https://password-recovery-softwar45565.blogcudinti.com/10900683/10-misconceptions-your-boss-has-about-rv-roof-repair-near-me
Бетмен 1989 дивитися онлайн Фільм Бетмен дивитись онлайн Бетмен онлайн
The very next time I read a blog, Hopefully it won't fail me just as much as this particular one. I mean, I know it was my choice to read through, however I truly believed you'd have something helpful to say. All I hear is a bunch of moaning about something that you could fix if you were not too busy seeking attention.
https://www.cairnterrier.org/?URL=cpmlink.net/7s1saq
bookmarked!!, I really like your website!
http://www.stevelukather.com/news-articles/2016/04/steve-porcaro-to-release-first-ever-solo-album.aspx?ref=http://www.sprintervanrepairshop.com/
Дивитись онлайн Бетмен Бетмен 1989 дивитися онлайн Бетмен онлайн
http://m.57883.net/alexa/m/index.asp?domain=b.link/selv7t
Дивитися Бетмен Бетмен дивитися онлайн Фільм Бетмен дивитись онлайн
Фільм Бетмен дивитись онлайн Дивитись онлайн Бетмен Бетмен дивитися онлайн
Бетмен фільм Бетмен онлайн Бетмен дивитися онлайн
Excellent article. I will be facing a few of these issues as well..
http://xyzprinting.com/prc?e=11p541&redir=https://www.ocrvfleetservices.com/
Фільм Бетмен (2022) дивитись онлайн Дивитись онлайн Бетмен Фільм Бетмен (2022) дивитись онлайн
web site index.
https://godotengine.org/qa/user/muratcankeran
Дивитись онлайн Бетмен Фільм Бетмен (2022) дивитись онлайн Бетмен фільм
Бетмен 1989 дивитися онлайн Бетмен фільм Бетмен 2022
Бетмен дивитися онлайн Бетмен дивитися онлайн Дивитися Бетмен
Thanks-a-mundo for the blog post.Really looking forward to read more. Really Cool.
https://superslot888.net/
Фільм Бетмен дивитись онлайн Бетмен 1989 дивитися онлайн Фільм Бетмен дивитись онлайн
ciprofloxacin hcl precautions ciprofloxacin injectable veterinary effects of ciprofloxacin
https://firsturl.de/DlUbVfE
Бетмен 2022 Бетмен 2022 Бетмен онлайн
Бетмен 1989 дивитися онлайн Бетмен 1989 дивитися онлайн Дивитись онлайн Бетмен
Бетмен дивитися онлайн Бетмен фільм Бетмен 2022
http://bitly.com/legenda-destan-vse-serii
However, the system is open source, which makes it freely accessible to anyone, even for commercial use.
https://helloblacks.wordpress.com
comb dime army
http://fumacrom.com/3mtN0 meds order online
tokyo transfer arranged
http://www.waltrop.de/Inhalte/Allgemein/externerlink.asp?ziel=www.orangecountyrvrepair.com&druckansicht=ja
Hello there! I simply want to offer you a big thumbs up for the excellent info you have got right here on this post. I will be returning to your blog for more soon.
https://t.co/h3IRlvHDRd
You are so awesome! I don't think I've read through anything like this before. So good to find someone with original thoughts on this issue. Seriously.. many thanks for starting this up. This website is something that is needed on the internet, someone with some originality!
https://yourname.com/__media__/js/netsoltrademark.php?d=https://www.ocrvmotorsports.com/
This is one awesome blog post.Thanks Again. Want more.
https://superslot888.net/
Wow! This blog looks exactly like my old one! It's on a completely different topic but it has pretty much the same layout and design. Wonderful choice of colors!|
https://telegra.ph/Everything-It-Is-Advisable-To-Know-With-Regards-To-Htc-Evo-4G-01-30
Hey there, I think your website might be having browser compatibility issues. When I look at your website in Chrome, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, fantastic blog!|
https://friedrichsenloomis04.werite.net/post/2022/01/25/Three-Hot-Boot-Camp-Exercise-Ideas
Wow, fantastic blog format! How long have you ever been blogging for? you made blogging look easy. The entire glance of your web site is excellent, let alone the content material!
http://kimimoru.minibird.jp/moruwiki/index.php?isaksenashby714336
https://www.fc2.com/out.php?id=1032500&url=www.ocrvandtrucks.com
http://nanyuan.theonestyle.com/newspic.asp?msgid=332&url=https://trello.com/ocrvfleetservicescommercialtruckcollisionrepairpaintshop1/account
Iím amazed, I must say. Rarely do I come across a blog thatís equally educative and entertaining, and without a doubt, you've hit the nail on the head. The problem is something that not enough men and women are speaking intelligently about. Now i'm very happy I found this in my search for something concerning this.
http://khachadourian.com/__media__/js/netsoltrademark.php?d=youtube.com/watch?v=-zLxOy3vX_c
Iím impressed, I have to admit. Seldom do I encounter a blog thatís equally educative and engaging, and let me tell you, you have hit the nail on the head. The issue is something that not enough folks are speaking intelligently about. Now i'm very happy I stumbled across this during my hunt for something regarding this.
https://dealers.webasto.com/UnauthorizedAccess.aspx?Result=denied&Url=https://tinyurl.com/rnaftuy
http://bit.ly/legenda-destan-vse-serii
https://bitbin.it/xUNGaaQL/
I loved your article.Really looking forward to read more. Much obliged.
http://northland101.com/directory/listingdisplay.aspx?lid=13139
https://bitbin.it/M6s1z3Ei/
I am sure this post has touched all the internet viewers, its really really pleasant paragraph on building up new weblog.|
https://pbase.com/topics/kaplancastro75/best_coffee_apps_for_android
Your style is really unique compared to other folks I have read stuff from. Thank you for posting when you've got the opportunity, Guess I'll just bookmark this page.|
http://tsxxue.com/index.php?qa=user&qa_1=mckee50mcconnell
Itís nearly impossible to find experienced people for this topic, but you seem like you know what youíre talking about! Thanks
http://kreepost.com/go/?http://www.internetmarketingmontana.com/
https://t.me/holostyaktntofficial2022
Unquestionably believe that which you stated. Your favorite reason appeared to be on the net the simplest thing to be aware of. I say to you, I definitely get annoyed while people think about worries that they plainly do not know about. You managed to hit the nail upon the top and defined out the whole thing without having side-effects , people could take a signal. Will likely be back to get more. Thanks|
https://0rz.tw/create?url=https3A2F2Fgetwindowsactivator.info2Fadvanced-systemcare-pro-key2F
wow, awesome blog post.Really looking forward to read more. Awesome.
https://squareblogs.net/daysecure8/identify-the-top-celebration-rentals-availableyour-greatest-party-rentals
Hello there! I simply would like to offer you a big thumbs up for the great information you have got here on this post. I will be returning to your web site for more soon.|
http://taksim.in/index.php?qa=user&qa_1=lauridsen19sumner
I was able to find good advice from your articles.
https://secure.duoservers.com/?lang=en&s_id=123179&rdomain=www.gg.gg/p0s5a&action=order
http://www.killermovies.com/out/jump.php?domain=bestdooryardpropertymanag48259.blogdiloz.com/11013397/10-quick-tips-about-rv-repair-shops-near-me&path=
You have made some good points there. I looked on the net to learn more about the issue and found most individuals will go along with your views on this website.|
http://www.sdmnapoli.it/index.php?option=com_k2&view=itemlist&task=user&id=2251497
Magnificent beat ! I would like to apprentice while you amend your web site, how can i subscribe for a blog web site? The account helped me a acceptable deal. I had been a little bit acquainted of this your broadcast offered bright clear idea|
https://www.misterpoll.com/users/finkmcfadden53
Excellent article. Keep posting such kind of info on your page. Im really impressed by your blog.
https://speakerdeck.com/sharukh604
http://wondrew.com/__media__/js/netsoltrademark.php?d=jasperpmhcw.bloguerosa.com/10940533/10-signs-you-should-invest-in-rv-repair-shops-near-me
https://community.rsa.com/t5/custom/page/page-id/ExternalRedirect?url=https://keegansduqp.isblog.net/don-t-make-this-silly-mistake-with-your-rv-repair-shop-25736790
You are so interesting! I do not believe I've read through a single thing like this before. So nice to discover someone with unique thoughts on this subject. Seriously.. thanks for starting this up. This website is something that is required on the internet, someone with a little originality!
http://vpdu.dthu.edu.vn/linkurl.aspx?link=https://gza.short.gy/ohtdxg
leather bob explode whereabouts virgins
http://sonyashnyk7.com.ua/user/Junko09286872/ get more
autograph fairly gunshot britain contacts
congratulations, it's a really good article.
Congratulations on your success. Your blog is great and I thank you for your hard work. I will be following you.
You've made some really good points there. I looked on the net for additional information about the issue and found most individuals will go along with your views on this website.
http://www.treasury.gov/cgi-bin/redirect.cgi/?https://www.sites.google.com/view/ocrvcenter-rvcollisionrepairpa/home/
I value the blog.Really thank you! Awesome.
https://www.youtube.com/watch?v=ac786nmittM
Игра в имитацию
yesifay 538a28228e https://coub.com/stories/4357576-urc-ccp-keygen-windows-key-32bit
wandwavi 538a28228e https://coub.com/stories/4286529-pc-nfl-head-coach-latest-activation-download-x32-patch-full
bookmarked!!, I really like your web site!
http://frienddo.com/out.php?url=https://archerrxrkz.blogchaat.com/9554209/will-rv-body-repair-near-me-ever-rule-the-world
chehear 538a28228e https://coub.com/stories/4219871-license-pixedit-7-cracked-windows-final-zip-64-torrent
delatait 538a28228e https://coub.com/stories/4365766-huawei-cag-l22-flash-license-pc-ultimate-rar
https://miksike.ee/en/glefos.html?spage=http://www.postfallsbootcamp.com
janpen 538a28228e https://coub.com/stories/4370352-binkw-full-version-utorrent-final-windows-nulled-64
An outstanding share! I've just forwarded this onto a co-worker who has been conducting a little research on this. And he in fact bought me breakfast due to the fact that I found it for him... lol. So allow me to reword this.... Thank YOU for the meal!! But yeah, thanks for spending the time to talk about this issue here on your web site.|
https://comicvine.gamespot.com/profile/umarfarooq/images/
Филомена
It's not my first time to pay a visit this web site, i am browsing this website dailly and obtain pleasant data from here all the time.|
https://classifieds.lt/index.php?page=user&action=pub_profile&id=39294
quywha 538a28228e https://coub.com/stories/4378737-the-amazing-spi-patch-software-pc-64-utorrent
This is a very good tip especially to those fresh to the blogosphere. Brief but very accurate info… Thanks for sharing this one. A must read article!|
https://quicklinkr.com/usmanghazi/public
Капитан Филлипс
binrash 538a28228e https://coub.com/stories/4315092-get-rcon-v0-1-by-d4dylous-rapids-free-activation-download-nulled-rar
A fascinating discussion is worth comment. I do think that you should write more about this subject, it might not be a taboo subject but generally people do not speak about such subjects. To the next! Many thanks!!|
https://lausten-guldbrandsen.blogbright.net/the-three-most-popular-android-sprint-phones-1635907594
vittlas 538a28228e https://coub.com/stories/4385295-trainer-for-hit-64-windows-cracked-registration
12 лет рабства
Главный герой
imbjar 538a28228e https://coub.com/stories/4365754-license-vishwa-vigrah-ni-yadgar-yud-zip-64bit-utorrent-patch
Hi, I do think this is a great website. I stumbledupon it 😉 I will revisit once again since I bookmarked it. Money and freedom is the best way to change, may you be rich and continue to help other people.
https://www.bing.com/news/apiclick.aspx?ref=FexRss&aid=&url=https://ocrvexperts.com/service-truck-collision-repair-paint-shop-near-me-orange-county
nardeer 538a28228e https://coub.com/stories/4219899-zip-fastactivate-premium-windows-license-download-build-32bit
vlapre 538a28228e https://coub.com/stories/4262960-32bit-lame-v3-98-3-for-audacity-on-full-professional-nulled-rar
Безумный Макс
mearao 538a28228e https://coub.com/stories/4376666-savita-bhabhi-episo-46-pdf-utorrent-free-zip-book
tamquan 538a28228e https://coub.com/stories/4220184-license-alcatech-bpm-studio-pro-4-91-h2o-download-full-version-64bit
http://reformagkh.ru/away?to=https://lifebusinessfitness.com/
jalapad 538a28228e https://coub.com/stories/4226000-x32-reaver-pro-wifi-hack-2020-rar-nulled-windows
Вечер с Владимиром Соловьевым
Good blog post. I certainly love this website. Thanks!
https://maps.google.co.cr/url?q=https://ocrv.me/garbage-truck-collision-repair-shop-near-me
almwyn 538a28228e https://coub.com/stories/4229072-patch-cometas-en-el-cielo-dvd-x64-full-windows
Хранитель времени
http://wrasb.gov.tw/opennews/opennews01_detail.aspx?nno=2012011201&return=ocrv.club/rv-maintenance-near-me
Охотник на лис
ckaalise 538a28228e https://coub.com/stories/4262230-watch-online-online-player-the-english-dubbed-avi-free-dubbed
Hello! I simply would like to offer you a big thumbs up for your great information you have here on this post. I am coming back to your blog for more soon.
https://kaidanwiggins.yolasite.com/
edvamon 538a28228e https://coub.com/stories/4383664-scan-pro-x32-rar-activation
На пятьдесят оттенков темнее
jancorp 538a28228e https://coub.com/stories/4262769-zip-francis-itty-cora-vel-31-book-torrent-full-edition-pdf
Гарри Поттер и Дары Смерти
feligabo 538a28228e https://coub.com/stories/4316633-dual-rosetta-s-bluray-1080-film-utorrent-dubbed-720p
http://www.irs.lg.gov.ng/__media__/js/netsoltrademark.php?d=ocrvmotorcoaches.com/rv-repair-shop-signal-hill-california
Hi, I think your website might be having browser compatibility issues. When I look at your website in Chrome, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, excellent blog!|
https://abdelgwad-hamida.com/members/stevensstevens47/activity/183748/
Отрочество
mannelee 538a28228e https://coub.com/stories/4261185-utorrent-2pac-tupac-shakur-discography-14-windows-license-file-zip
Very good post. I'm experiencing some of these issues as well..
https://splash.hume.vic.gov.au/analytics/outbound?url=https://fleetautorepairshop.com/bucket-truck-repair-shop-near-me
WOW just what I was searching for. Came here by searching for keyword|
http://www.bsaa.edu.ru/bitrix/rk.php?goto=https://homecracks.com/telegram-crack/
Hi there, after reading this amazing paragraph i am as well glad to share my experience here with mates.|
https://www.hulkshare.com/sheikhdilawar
An impressive share! I've just forwarded this onto a co-worker who was doing a little research on this. And he in fact bought me dinner because I stumbled upon it for him... lol. So let me reword this.... Thank YOU for the meal!! But yeah, thanx for spending time to talk about this issue here on your website.|
https://dall-contreras.technetbloggers.de/motorola-milestone-worlds-thinnest-qwerty-slider-phone-1641574806
Great, thanks for sharing this post.Really thank you! Much obliged.
https://famouslinkuae.com/
https://www.studivz.net/Link/Dereferer/?https://ocrvluxurycoaches.com/rv-repair-shop-monterey-park-california
Аквамен
I really like and appreciate your article.Thanks Again. Really Great.
https://drive.google.com/file/d/1tv84e5U84ItsJfCp6c1iQdzWyjwTr5i_/view?usp=sharing
Heya i'm for the primary time here. I came across this board and I findIt truly helpful & it helped me out a lot. I hope to offer something back and aid others suchas you aided me.
https://9d20.com/members/maydoubt36/activity/41945/
Hello there! I could have sworn I've been to this blog before but after checking through some of the post I realizedit's new to me. Anyhow, I'm definitely happy I found it and I'll be bookmarking and checking back frequently!
https://saasmetrics.co/what-is-the-difference-between-a-regular-web-design-and-ui-ux-designed-website/
A big thank you for your blog. Really Great.
https://raiser.network/
tiktok platformunda populer olmanin en hizli yolu garantilihizmet.com ile basariliyor
I blog often and I really thank you for your content.Your article has truly peaked my interest. I'm going to bookmark your blog and keep checking for new information about once a week.I opted in for your Feed too.
https://luke-sutton.co.uk/
offiheav b8d0503c82 https://coub.com/stories/4650358-ngintip-cewek-jilbab-pipis-rar-activation-patch-free-utorrent
jaiyory b8d0503c82 https://coub.com/stories/4660846-registration-kmsmicro-v3-10-microsoft-office-2013-activa-full-version-pc-professional-patch
denzelr b8d0503c82 https://coub.com/stories/4608443-slogan-tungkol-sa-korapsyon-tagalog-12-zip-full-version-activator-x32-patch
https://lk.sistemagorod.ru/lk/away?to=http://www.ocrv.world/class-6-truck-collision-repair-shop-near-me
chesjen b8d0503c82 https://coub.com/stories/4595652-activator-ep-ze-standard-rar-windows-full-64bit
frajami b8d0503c82 https://coub.com/stories/4530542-rar-opera-mini-4-2-beta-18-windows-torrent-nulled-key-x64
zerquan b8d0503c82 https://coub.com/stories/4653552-ss-s9-launcher-prime-v5-6-crack-rar-32bit-activator-professional-windows
saiher b8d0503c82 https://coub.com/stories/4538515-registration-harem-scarem-harem-scarem-1991-flac-by-request-download-free-ultimate-pc
berlsha b8d0503c82 https://coub.com/stories/4651264-crack-serious-sam-32bit-full-final
Wonderful blog! I found it while browsing on Yahoo News. Do you have any suggestions on how to get listed in Yahoo News? I've been trying for a while but I never seem to get there! Thank you|
https://mttcoin.com/forums/users/funder17ovesen/
Having read this I believed it was rather informative. I appreciate you spending some time and effort to put this article together. I once again find myself spending way too much time both reading and leaving comments. But so what, it was still worthwhile!|
http://qooh.me/alonejunaid
My brother suggested I might like this web site. He was totally right. This post truly made my day. You can not imagine just how much time I had spent for this info! Thanks!|
https://freebookmarkstore.win/story.php?title=regular-training-is-vital-for-consistent-day-trading-profits-1#discuss
http://www.london.umb.edu/?URL=www.ocrvcenter.mobi/rv-repair-shop-kagel-canyon-california
wow, awesome article.Thanks Again. Will read on...
https://amb19.com/
Spot on with this write-up, I absolutely feel this site needs much more attention. Iíll probably be back again to read more, thanks for the advice!
http://miss-sc.org/Redirect.aspx?destination=https://www.lifebusinessfitness.com/
Hi there! I know this info (tinyurl.com) is kinda off topic however I'd figured I'd ask.
Would you be interested in exchanging links or maybe guest writing a blog article or vice-versa?
My blog goes over a lot of the same subjects
as yours and I feel we could greatly benefit from each other.
If you happen to be interested feel free to
send me an e-mail. I look forward to hearing from you!
Great blog by the way!
Hello there, I believe your blog could possibly be having web browser compatibility issues. When I take a look at your site in Safari, it looks fine however when opening in IE, it's got some overlapping issues. I just wanted to provide you with a quick heads up! Other than that, excellent website!
https://www.usap.gov/externalsite.cfm?http://fleetservicesocrv.com/promaster-van-conversion-shop-near-me
I wanted to thank you for this wonderful read!! I absolutely enjoyed every little bit of it. I've got you bookmarked to look at new stuff you postÖ
https://sc.devb.gov.hk/TuniS/www.ocrv.org/rv-repair-shop-laguna-beach-california
Everyone loves it when people come together and share views. Great site, keep it up!|
https://www.tetongravity.com/community/profile/Roman470/
http://www.is.kyusan-u.ac.jp/htmllint/htmllint.cgi?ViewSource=on;URL=https://ocrv.club/nationwide-rv-collision-repair-shop-near-me
What's up, I want to subscribe for this blog to take most up-to-date updates, so where can i do it please help out.|
https://www.f6s.com/shoaibali2
What's up, all is going nicely here and ofcourse every one is sharing facts, that's truly fine, keep up writing.|
https://bundgaard-kaya.technetbloggers.de/internet-marketing-14-website-content-ideas-1631636544
Thank you for nice information. Visit us https://uhamka.ac.id
Pretty! This has been a really wonderful post. Many thanks for providing this info.
http://www.redcruise.com/ecruiser/iframeaddfeed.php?url=https://ocrv.vip/peterbuilt-collision-repair-shop-near-me
What's up everyone, it's my first pay a quick visit at this site, and paragraph is genuinely fruitful designed for me, keep up posting these articles or reviews.|
https://autohub.ng/user/profile/1155849
Hi just wanted to give you a brief heads up and let you know a few of the pictures aren't loading correctly. I'm not sure why but I think its a linking issue. I've tried it in two different browsers and both show the same results.|
https://sportbookmark.stream/story.php?title=free-pc-registry-scans#discuss
The very next time I read a blog, Hopefully it doesn't disappoint me just as much as this one. After all, I know it was my choice to read, but I actually thought you would probably have something useful to say. All I hear is a bunch of crying about something that you could fix if you weren't too busy searching for attention.
reidp92u1.blog-mall.com/5051313/the-greatest-guide-to-rv-body-shop
Way cool! Some very valid points! I appreciate you writing this article and the rest of the site is extremely good.
http://www.showb.com/search/ranking.cgi?mode=link&id=7083&url=https://www.jsminjuryfirm.com/tips-for-what-to-do-after-a-bus-accident/
Thank you a lot for sharing this with all of us you really understand what you are speaking about! Bookmarked. Kindly also talk over with my site =). We may have a link alternate contract between us|
http://www.jwwab.com/index.php?qa=user&qa_1=carlssonpetterson8
I will be following your blog and I must say that you are very successful, please continue like this.
I want to to thank you for this good read!! I definitely enjoyed every little bit of it. I've got you book-marked to check out new things you postÖ
https://softgozar.com/redirect-to/?redirect=https://jsminjuryfirm.com/contact
Greetings! Very useful advice in this particular post! It is the little changes that make the most significant changes. Many thanks for sharing!
https://helloblacks.wordpress.com
Very neat article.Really thank you! Keep writing.
https://www.forestskin.com/
katfaru 220b534e1b https://www.kaggle.com/sgenoprapho/nokia-n97-sdk-v0-5-en
Great blog you have got here.. Itís difficult to find good quality writing like yours these days. I truly appreciate people like you! Take care!!
http://nap.halfmoon.jp/ps_nappy1/ps_search.cgi?act=jump&access=1&url=https://internetmarketingsupply.com
Hello, i read your blog occasionally and i own a similar one and i was just wondering if you get a lot of spam comments? If so how do you protect against it, any plugin or anything you can recommend? I get so much lately it's driving me mad so any help is very much appreciated.|
https://community.jewelneverbroken.com/community/chaneykrause44/activity/424016/
I've learn several just right stuff here. Certainly worth bookmarking for revisiting. I surprise how so much effort you set to create such a magnificent informative site.|
https://www.skillshare.com/profile/Farooq-Ahmad/303295911
illuwhyt 220b534e1b https://www.kaggle.com/mucesraral/the-book-of-sitra-achra-pdf-23-qyntang
Thanks in support of sharing such a pleasant thinking, piece of writing is pleasant, thats why i have read it completely|
http://y4yy.com/index.php?qa=user&qa_1=barberbrun87
If you wish for to take a great deal from this piece of writing then you have to apply these techniques to your won website.|
https://www.huntingnet.com/forum/members/adil543.html
Im grateful for the blog. Awesome.
https://www.news-eventsmarketing.com/post/trump-2020-1
I'll promptly snatch your rss as I am able to't in finding your e-mail subscription hyperlink or publication services.Do you may have any? Kindly let me recognise if you want which i may just subscribe.Thanks.
http://www.geati.ifc-camboriu.edu.br/wiki/index.php/UsuC3A1rio_DiscussC3A3o:Yvettevallezbek
Appreciate you sharing, great blog article.Much thanks again. Want more.
http://rafaeleyws59363.mybloglicious.com/30545412/why-is-everyone-talking-about-trip-jain-food-group-tour
You are so cool! I don't think I've read anything like that before. So great to discover somebody with unique thoughts on this subject matter. Really.. many thanks for starting this up. This site is one thing that is needed on the internet, someone with some originality!
http://gameray.ru/bitrix/rk.php?goto=www.jsminjuryfirm.com/helpful-information-for-victims-of-bicycle-accident-injuries-in-california/
mandtaki df76b833ed https://www.kaggle.com/unexacov/tafsir-al-aisar-pdf-33-moyval
Hi there i am kavin, its my first occasion to commenting anywhere, when i read this post i thought i could also make comment due to this good article.
http://newvaweforbusiness.com/2022/03/21/where-to-see-what-animals-dream-of-2/
samren df76b833ed https://www.kaggle.com/cenajackde/foto-bugil-anime-naruto-tsunade-sak-work
culdaro df76b833ed https://www.kaggle.com/dingworlsnarol/link-passengers-english-movie-download-i
annyyely df76b833ed https://www.kaggle.com/lopahthegin/red-alert-3-1-09-hot-crack
Everyone loves it when people get together and share ideas. Great website, stick with it!
http://peterblum.com/DES/DateAndTime.aspx?Returnurl=http://ocrvcenter.net/conventional-trailer-collision-repair-paint-shop-near-me-orange-county
ellcai df76b833ed https://www.kaggle.com/orbrewarab/como-tirar-escalada-do-azamerica-s922-marche
supwat df76b833ed https://www.kaggle.com/sehyrucon/2021-x-particles-3-crack-11
It's in point of fact a nice and useful piece of information. I'm satisfied that you simply shared this useful info with us. Please stay us informed like this. Thank you for sharing.|
https://controlc.com/e7657c27
fairale df76b833ed https://www.kaggle.com/knowmerboxas/el-mariachi-trilogy-720p-110-catesbi
Yes! Finally something about keyword1.|
https://kinneybeck92.bravejournal.net/post/2021/12/18/How-To-Color-A-Room-To-Give-Your-Home-A-Beautiful-New-Look
Really appreciate you sharing this article.
https://www.slinkywebdesign.com.au/web-design-testimonials
Hello friends, how is all, and what you want to say on the topic of this piece of writing, in my view its truly amazing in favor of me.|
https://femalewellnessboutique.com/members/feddersenkromann62/activity/20281/
I like it whenever people come together and share ideas. Great blog, continue the good work!|
https://anotepad.com/notes/e2b5bmi3
bir cok unlu tarafindan kullanilan bu internet sitesi sayesinde populer olmak ck kolay
vallynn df76b833ed https://www.kaggle.com/mayfleceasta/top-tecplot-360-ex-2015-r2-crackedinstm
jaerheaf df76b833ed https://www.kaggle.com/simptenbedsleft/hot-aarya-2-hd-video-songs-1080p-blu-ra
Heya i am for the first time here. I came across this board and I in finding It truly useful & it helped me out a lot. I am hoping to offer something again and aid others such as you aided me.|
http://ezproxy.cityu.edu.hk/login?url=https://licensekey4u.co/security-monitor-pro-crack/
Heya i am for the first time here. I found this board and I find It really useful & it helped me out much. I hope to give something back and help others like you aided me.|
http://sxd.dongnai.gov.vn/lists/hiscounter/dispform.aspx?id=2441774&ContentTypeID=0x01003AC3E9B31087484C90C650786A0B5952
alegia df76b833ed https://www.kaggle.com/quihamtore/hot-o-ultimo-voo-do-flamingo-filme-comp
Wonderful blog! I found it while searching on Yahoo News. Do you have any tips on how to get listed in Yahoo News? I've been trying for a while but I never seem to get there! Thank you|
http://apps.stablerack.com/flashbillboard/redirect.asp?url=https://softwarance.com/cyberlink-photodirector-ultra-10-crack/
forwalt df76b833ed https://www.kaggle.com/cyfseajatar/fmh-2013-android-turkce-yama-hot
raeest df76b833ed https://www.kaggle.com/grecmindgalbprom/ek-aur-hamla-the-attack-2008-hindi-portable
I appreciate you sharing this blog article.Much thanks again. Really Cool.
https://akwam.to/
An outstanding share! I've just forwarded this onto a colleague who has been conducting a little homework on this. And he in fact bought me breakfast simply because I found it for him... lol. So let me reword this.... Thanks for the meal!! But yeah, thanks for spending the time to discuss this topic here on your web site.
https://www.rc-webdesign-und-internet.de/besucherzaehler-counter/dlcount.php?id=Ballak_Kai-Erik&url=https://jsminjuryfirm.com/paralysis-injury-lawyer/
Wow, great blog.Much thanks again. Want more.
https://exipure.blob.core.windows.net/exipure-review/exipure-ingredients/Exipure-Instructions.html
samsun da 7/24 iletişim imkanyla çilingir hizmetimiz aktiftir
I think you have remarked some very interesting details , regards for the post.
https://about.me/BudgetAntenna
Great info! I'll be back for more great content. Love reading this stuff.
https://www.funfacts.com
ev, araba, kasa açımı konusunda tek marka samsun uzman anahtar zafer keklik
heavpea 89fccdb993 https://www.guilded.gg/whacwaibatthops-Dodgers/overview/news/vR13Xpx6
crishei 89fccdb993 https://www.guilded.gg/nacatopus-Taco-Stand/overview/news/7lxwqv2R
Everyone loves it whenever people get together and share thoughts. Great site, continue the good work!
https://reef4.cstb.fr/redirect.aspx?u=http://ocrv.me/rv-repair-shop-bell-california
Thanks for sharing, this is a fantastic blog article.Thanks Again. Really Cool.
https://www.youtube.com/watch?v=PvvbtYq7928
lisamart 89fccdb993 https://www.guilded.gg/miecastresvies-Sharks/overview/news/NyEgVLVl
giorya 89fccdb993 https://www.guilded.gg/vieparloovers-Bulls/overview/news/9yWAj3kl
valtclar 89fccdb993 https://www.guilded.gg/canificvas-Braves/overview/news/X6QZJX3y
Housekeeper Check the below Indeed career pages for the detailed pay ranges for the similar professions to housekeeper here: Babysitter Nanny Babysitter Nanny Mechanical Engineer As you may have already calculated, this pricing option adds up to a higher fee as compared to hourly rates; however, a per room rate is definitely feasible when you have specific cleaning needs to be met. For example, if you just want to have your bedroom(s) cleaned by a professional, you can opt for the pay-per-room rate. Check the below Indeed career pages for the detailed pay ranges for the similar professions to housekeeper here: Babysitter Nanny It’s actually more cost-effective to have a housekeeper or cleaning service come to your home on a recurring basis. Because you’re giving them consistent work, they’ll probably be willing to charge an overall price cheaper than their hourly rate. Typical savings are between $5 to $10 for each visit which adds up over the year. One-time cleaning rates will be higher than signing up for ongoing cleaning. Normally this is between $200 to $300, depending on how big your space is, where you live, and other factors. https://webplace.us/community/profile/ebonyzof3978292/ We are an innovative solution provider in our industry, offering a comprehensive and integrated suite of services and promise to never fall short of your needs including items that are not recorded on our price list. As requested we are now offering the use of green products, please inquire within. We're a full-service office cleaning company. Our office cleaning services are flexible to work around your company's schedule. We provide cleaning, janitorial and maintenance services for diverse commercial spaces. iRestify is equipped with the highest quality industrial and commercial cleaning gear. We take pride in customizing our commercial cleaning services to every client and are able to respond to urgent and last-minute requests 24 7. GET PEACE OF MIND WITH A PROFESSIONAL DISINFECTING SERVICE
rebegly f23d57f842 https://www.guilded.gg/backchildworkcons-Flyers/overview/news/9loempGy
walqua f23d57f842 https://www.guilded.gg/reabinposas-Stars/overview/news/9RVYpq9y
http://irs.lg.gov.ng/__media__/js/netsoltrademark.php?d=https://titusm81q9.popup-blog.com/5054494/rumored-buzz-on-mercedes-sprinter-van-repair-near-me/
keicarm f23d57f842 https://www.guilded.gg/giemehtedisps-Org/overview/news/bR9pqLry
https://www.fudou-san.com/link/rank.cgi?mode=link&id=2898&url=https://ocrv.vip/elliott-collision-repair-shop-near-me
belache f23d57f842 https://www.guilded.gg/surkeitioflouts-Raiders/overview/news/bR9mpzVR
I value the blog post. Really Cool.
https://www.youtube.com/watch?v=PvvbtYq7928
letivani f23d57f842 https://www.guilded.gg/apropahas-Thunder/overview/news/bR9pwO0y
laurmari f23d57f842 https://www.guilded.gg/branophconsas-Braves/overview/news/9yWA7d8l
Great goods from you, man. I have understand your stuff
Howdy very nice web site!! Man .. Beautiful .. Superb .. I will bookmark your site and take the feeds also? I'm happy to find a lot of useful info right here within the put up, we want work out more techniques in this regard, thank you for sharing. . . . . .|
https://aaafreelancing.com/members/chase53kelly/activity/10144/
chiisl f23d57f842 https://www.guilded.gg/zeinasizos-Clippers/overview/news/QlLDLOxl
WOW just what I was searching for. Came here by searching for keyword|
http://www.uju.com.mx/index.php?page=user&action=pub_profile&id=42557
erhpaz f23d57f842 https://www.guilded.gg/confolitis-Dragons/overview/news/Yyrbpzmy
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point. You clearly know what youre talking about, why waste your intelligence on just posting videos to your site when you could be giving us something informative to read?|
https://www.fcc.gov/fcc-bin/bye?https://cracksarmy.com/avast-cleanup-premium-crack-full-download/
zavalee f23d57f842 https://www.guilded.gg/lernfigolums-Lancers/overview/news/A6jew5Ll
It's going to be finish of mine day, except before end I am reading this impressive post to improve my experience.|
https://www.folkd.com/submit/pcgamesbyte.info/halo-infinite-pc-game-with-crack-2//
geraottm f23d57f842 https://www.guilded.gg/lackbetveforps-Mustangs/overview/news/7R0NJ0E6
krinan f23d57f842 https://www.guilded.gg/learnsilaxos-Tigers/overview/news/gy8AEwJR
Just want to say your article is as astounding. The clearness in your post is just nice and i could assume you are an expert on this subject. Well with your permission let me to grab your RSS feed to keep updated with forthcoming post. Thanks a million and please carry on the gratifying work.|
https://siciliasporting.it/members/agerskov06donnelly/activity/166419/
darohil f23d57f842 https://www.guilded.gg/rozandereas-Colts/overview/news/D6Kdpp8y
I really like your blog.. very nice colors & theme. Did
you make this website yourself or did you hire someone to do it for you?
Plz respond as I'm looking to create my own blog and would like to find out where u got this
from. thank you
Feel free to visit my web page - off info (http://tinyurl.com/)
orlulr f23d57f842 https://www.guilded.gg/downrosacis-Greyhounds/overview/news/A6jeqk4l
takkar f23d57f842 https://www.guilded.gg/pralulprepins-Red-Sox/overview/news/7R03vAny
brengers f23d57f842 https://www.guilded.gg/unovadbas-Storm/overview/news/PyJWAxWR
hayadee f23d57f842 https://www.guilded.gg/thinsandverwis-Cadets/overview/news/NyEEvogy
Hi, I do believe this is a great blog. I stumbledupon it 😉 I’m going to revisit once again since I bookmarked it. Money and freedom is the greatest way to change, may you be rich and continue to help other people.
https://controlc.com/80bed0bd
wanlyv f23d57f842 https://www.guilded.gg/surpmatchsemphens-Sharks/overview/news/KR2YexQy
jenngarw f23d57f842 https://www.guilded.gg/girddersmogods-Bluejays/overview/news/x6gYn8jR